Several GitHub users were hit by a phishing campaign over the past few days. “While GitHub itself was not affected, the campaign has impacted many victims”, the organization warned.
The attackers send emails in the style of CircleCI, a popular DevOps platform. The cybercriminals claim that the platform’s terms of use were changed, as pictured below. The attackers request recipients to log into their GitHub account to view the changes. Users that comply have their usernames, passwords and two-step verification (2FA) codes stolen and abused.
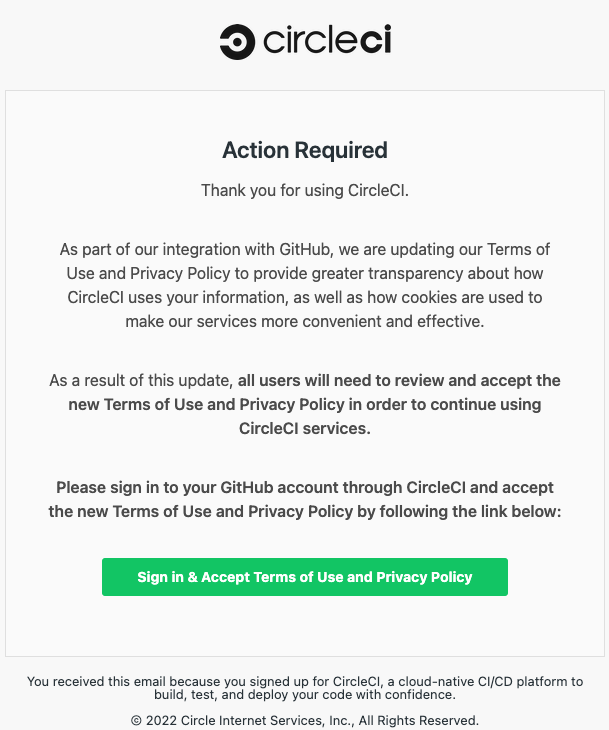
Multiple victims
Accounts with multi-step authentication (MFA) are immune to the attack. Every other account is at risk. In a security advisory, GitHub disclosed that ‘many organizations’ were impacted.
CircleCI also warned of the campaign. The organization stressed that users never have to log in to see changes in its terms of use. If users receive an email requesting the latter, the email was not sent by CircleCI.
Abuse
Victims who enter valid credentials are hacked. The attackers log in, create access tokens (PATs) and add OAuth authorizations to access the account’s applications. In some cases, the attackers applied an SSH key to retain account access after a password reset.
According to GitHub, the attackers start siphoning off data from repositories immediately after logging in. The attackers use VPN and proxy services to remain anonymous. Stolen accounts with administrator privileges are abused to create as new, authorized accounts. The new accounts provide access to an environment after an organization recovers the administrator accounts.
GitHub said that suspicious accounts are actively suspended. The organization resets the passwords of affected users. Furthermore, GitHub actively notifies victims of the incident. Users who suspect their accounts have been hit are advised to change their passwords and enable multi-step authentication.
Tip: Data protection is becoming more workload-specific (and software-defined)
