
Security

Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
Timeline

Old encryption technique in RADIUS protocol opens doors for hackers
Authentication protocol used extensively in corporate networks

How CrystalRay steals data using open-source software
Open-source is for everyone, including cybercriminals

Exclusive Networks possibly goes private for more than 2 billion euros
French cybersecurity specialist Exclusive Networks may disappear from the stock market. A consortium of priva...
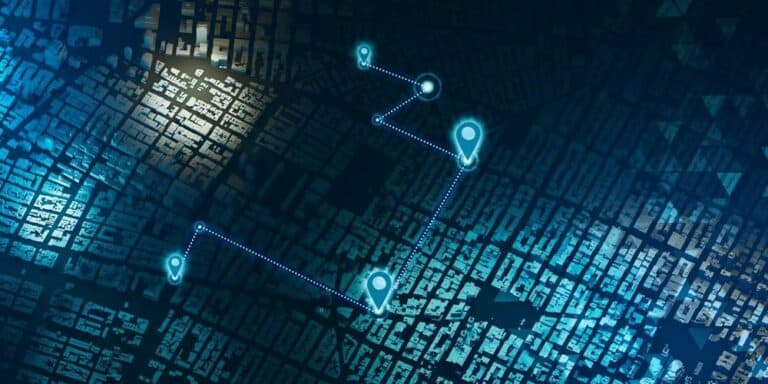
How Apple’s location API gives away Wi-Fi network data worldwide
Apple's Wi-Fi Positioning System (WPS) allows tech-savvy individuals to map Wi-Fi access points (APs) worldwi...

Companies increasingly ‘re-victimized’ by cybercriminals
Cybercriminals are increasingly trying to extort companies multiple times when their data has been captured. ...

Netherlands disrupts Russian disinformation campaign
The Dutch intelligence services AIVD and MIVD, in cooperation with the National Police, have taken offline a ...

Hackers steal sensitive customer data at Fujitsu undetected
In March, hackers stole sensitive information from Fujitsu customers. The company says it was not a ransomwar...

European consumers worry about online security and AI influence
Europeans are quite concerned about digital identity theft and the potentially detrimental role of AI in onli...

Ticketmaster tickets for 154 major concerts leaked
Hackers continue to extort Ticketmaster after the major data leak in May of this year. Recently, they leaked ...

Former ASML CEO Wennink: conflict with China based on politics, not numbers
Former ASML CEO Peter Wennink is still very troubled by trade restrictions imposed by the United States on AS...