Suspicious emails usually appear to come from Microsoft or Amazon. However, criminals are becoming increasingly cunning with the brands they mimic, so potential victims do not readily recognize the deception.
Mimecast looked at an overview of criminal activity through email campaigns in its October-December 2023 Threat Intelligence Report. In it, the security company also offers analysis for all of 2023. The company analyzed data from 1.7 billion emails per day on behalf of 42,000 customers.
Criminals typically impersonate legitimate companies in phishing emails. Microsoft is by far the most common disguise, with Amazon only as a temporary substitute when the online store is working overtime in the two weeks leading up to Black Friday. However, a change in tactics can gradually be seen: local brands are increasingly being imitated. Potential victims trust the authenticity of a message from a local bank, online stores and travel companies relatively quickly. If attackers are aware of the specific services a target uses, this tactic is particularly dangerous. How do attackers manage to better target their targets? And who are those targets?
Small targets, greater chance of success
Mimecast notes that attackers continue to innovate. Like legitimate industries, the cybercrime world has become an avid AI user. Generative AI tools yield higher effectiveness for criminals because they can generate more convincing phishing emails. Translations that tap into local context also make criminals goed phishers in countries they don’t even speak the language of. If a phishing email talks about current issues or responds to local laws, people tend to trust it rather quickly.
This specificity is accompanied by an emphasis on smaller organizations as victims. This makes sense, as regional players continually expect emails from locally active companies. An average SME employee faced more than 120 attack attempts last year, while personnel in a large company could count on about 60 attacks. The emphasis on SMBs can be explained by the fact that a higher proportion of the workforce performs critical roles. This means a greater chance of capturing sensitive data and fewer layers of protection than for large companies. In addition, attackers focus above all on stealing credentials, something that can do more damage to SMEs because they often rely almost entirely on external cloud services.
Increasingly, travel companies and hospitality companies are targets of these attacks. HR departments and recruitment agencies can count on the most attention, but activity from cybercriminal towards those targets decreased slightly. It seems that criminals are shifting their attention toward new victims, which suggests a greater chance of success there.
Changed attack techniques
In addition to the targets, the attack techniques are also shifting. For the first time, victims are more likely to click on a bad link than a malicious attachment. Classic malware is therefore shifting somewhat into the background: stealing credentials is preferred. The cloud environment of SMEs can therefore be compromised and lead to a ransomware incident. Clicking on a link can be enough to steal credentials. Tokens and account identifiers can be pulled directly from a Google Chrome session to infiltrate.
Also read: Cisco Identity Intelligence adds a vital element to cybersecurity
Instead of malware, attackers are also increasingly using quishing, or abusing QR codes to hide rogue links. According to Mimecast, quishing has now “moved from a niche attack methodology to the mainstream.” The use of QR codes skyrocketed during the corona pandemic, so the concept is now pretty well established. However, employees still don’t always seem to realize that they shouldn’t simply trust such codes. Without their own security departments, it is obvious that smaller organizations are less likely to realize that this attack technique has become popular. In any case, the danger is omnipresent: Mimecast detected 3.5 million quishing emails a day last year.
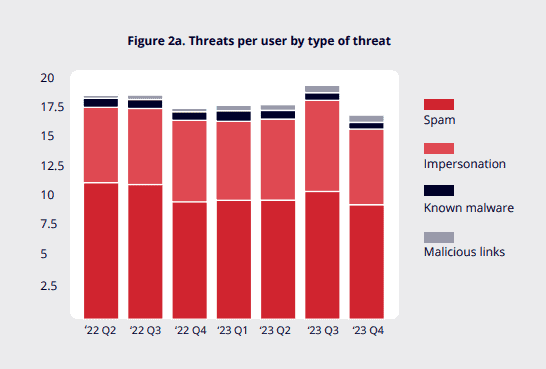
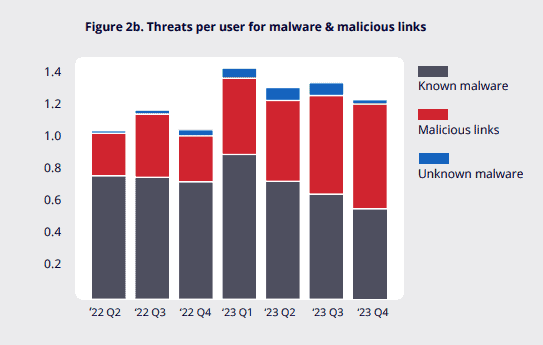
While the number of potential targets is increasing, the number of cybercrime groups is actually decreasing. The foursome of LockBit, Cl0p, ALPHV/BlackCat and Play collectively account for 88 percent of all ransomware activity. ‘Associates’ distribute the malicious software on behalf of these parties, often with hard bargaining rules so that the ransomware exploit is maximized. These groups are particularly persistent, as demonstrated recently when LockBit rebounded fairly quickly after an international operation.
Abusing big brands
Large companies still unintentionally play a major role in cybercrime. For example, Mimecast cites an example of an attacker who sent a link to a counterfeit Microsoft SharePoint server through a legitimate marketing service. Office 365 authentication is also a prime target.
To stage attacks, rogue users need to disguise suspicious links as best they can. One such technique is to take over subdomains of legitimate large companies. Campaigns via domains from MSN, VMware, McAfee and eBay, among others, managed to fool users. Importantly, in many cases these domains get through the spam filter and other security measures. So those who think their own inbox is well protected may mistakenly believe they are safe.
Measures to take against brand spoofing
Because criminals are focusing more on smaller targets, these organizations need to be better prepared than ever. Mimecast recommends extra protection for personnel in critical roles. Sales and executives should not be able to run code. IT admins, in turn, should be monitored for anomalous behavior. As for QR, Mimecast states that default image loading should be prevented. Another aspect of security in this area is simply educating employees about the changing cyber landscape. New threats in this area continue to ensure that organizations must be aware of more innovative methods of attack.
In general terms, Mimecast recommends reducing the attack surface, for example by making stolen credentials less damaging. In this regard, a zero-trust approach is of great importance, so that sensitive data cannot be accessed simply with login credentials alone and as few users as possible have access.
Those who want to prevent their own domain from being misused must, in part, hope that attackers overlook them. After all, any criminal can attempt to emulate any company. Nevertheless, there are tools, for example from Check Point, to gain insight into possible occurrences of brand spoofing abusing your organization. In any case, your own Web domain can be protected with DMARC (Domain-based Message Authentication, Reporting & Conformance), among others. A limited number of IP addresses should be able to send e-mails on behalf of the company. Likewise, customers should be aware of how you communicate as an organization. A crisis plan should be ready so that there is a quick way to act if your own company is replicated.
