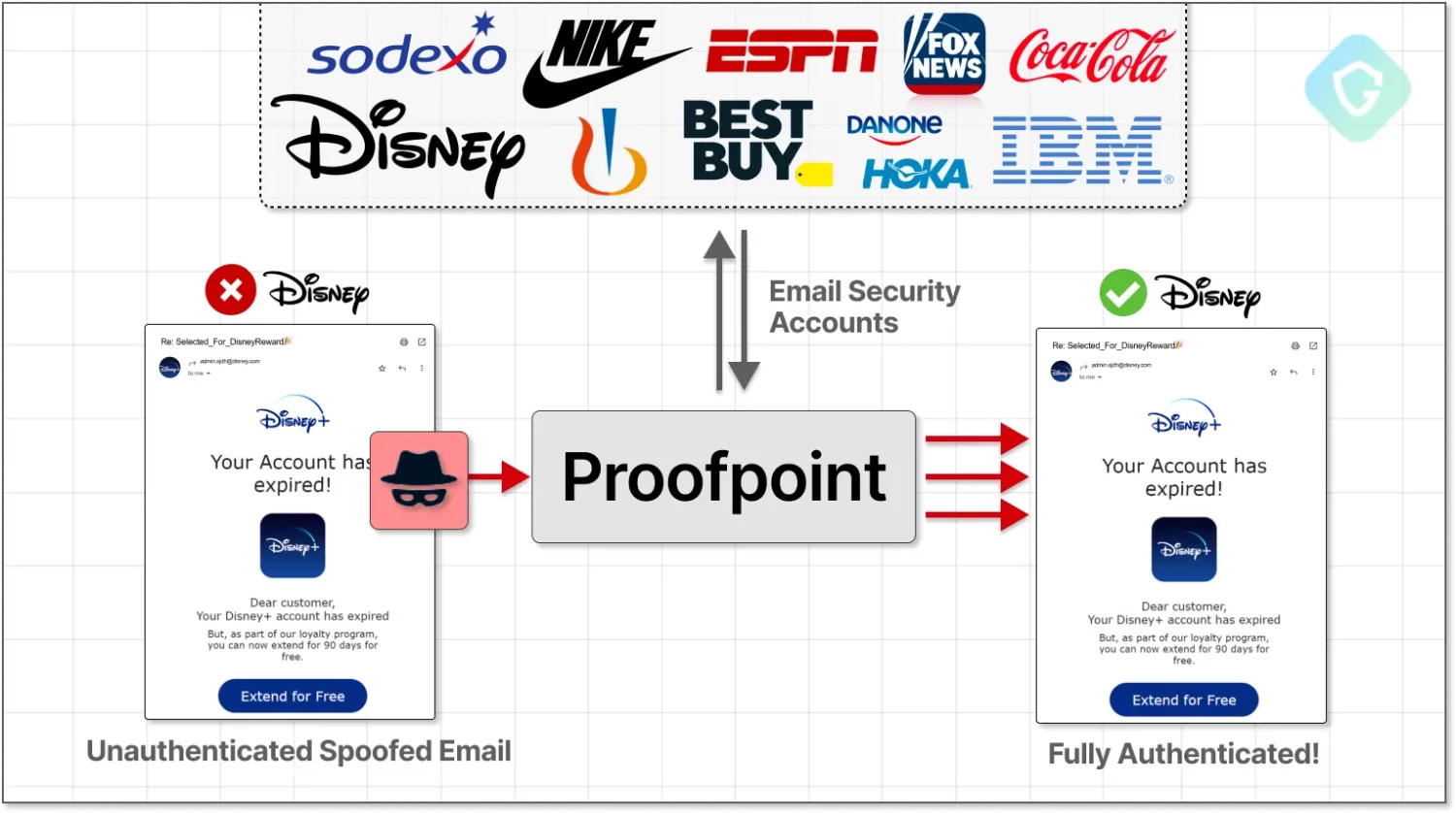
A critical exploit in email security provider Proofpoint’s service has caused millions of spoof emails to be sent that appeared to come from major companies such as Disney, IBM, Nike and Coca-Cola. They actually came from cybercriminals abusing official email relays with authenticated SPF and DKIM signatures. The vulnerability has since been fixed.
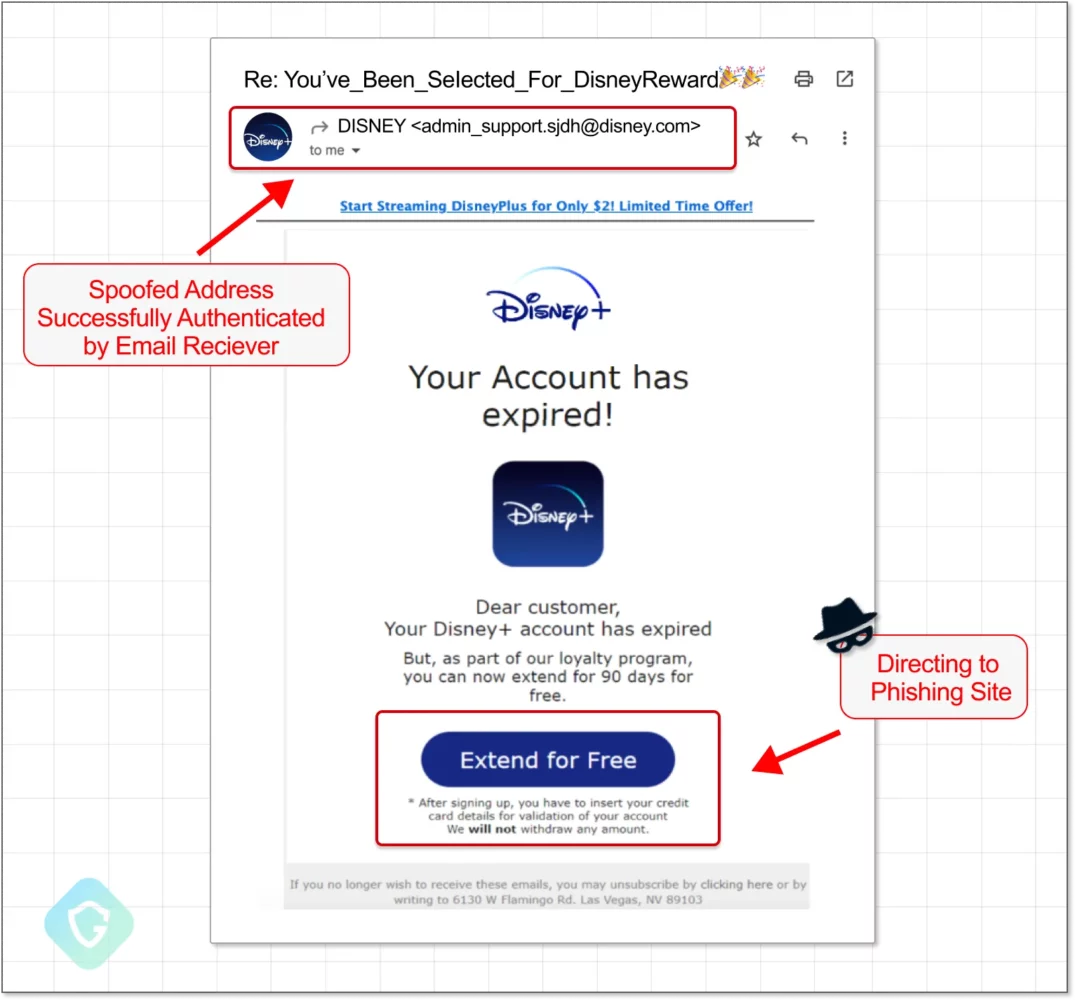
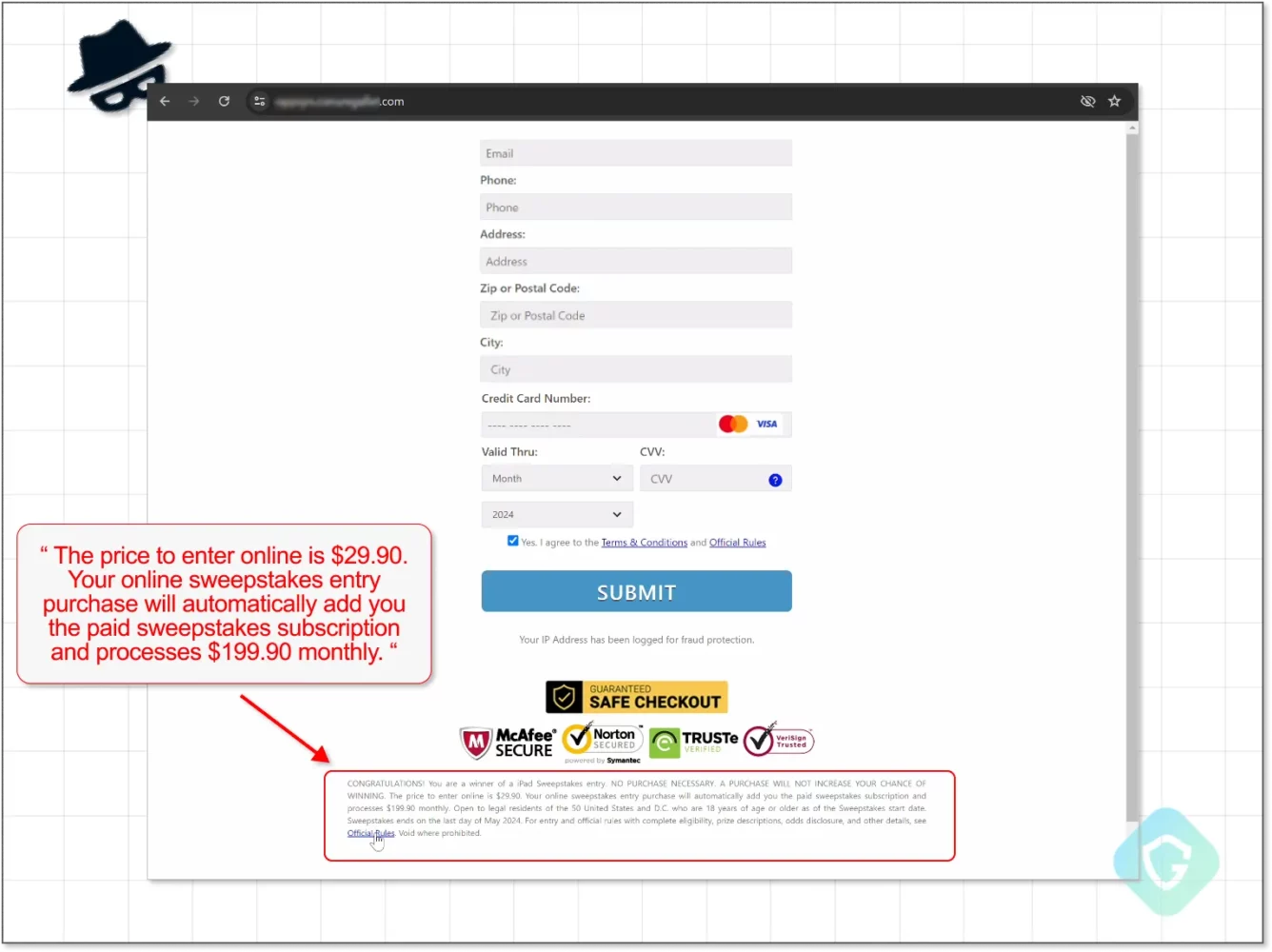
The phishing emails often mimicked well-known brands, supposedly informing recipients about account expiration or payment requests. The criminals thus managed to steal credit card information and, in some cases, even steal money from victims.
The campaign has been dubbed ‘Echospoofing’ by the criminals. Security company Guardio Labs reported on the case and worked with Proofpoint to identify and eventually stop the campaign.
Authentic-looking emails
The unusual thing about the spoofing method is that the criminals used a properly configured Sender Policy Framework (SPF) and the correct Domain Keys Identified Mail (DKIM) signatures. This not only allowed the emails to bypass security measures but also made them look particularly authentic to recipients.
Source: Guardio Labs
Millions of emails sent
The spoofing campaign began in January of this year, with an average of 3 million emails sent daily. It peaked in early June, with some 14 million daily emails. The emails came from one family of relay servers, i.e. pphosted.com, belonging to Proofpoint. Guardio Labs discovered the campaign in May and worked with Proofpoint to stop it.
The criminals used SMTP servers to create forged emails and sent them through Proofpoint’s servers using compromised or rogue Microsoft Office 365 accounts.
Configuration misused
These emails, sent through Virtual Private Servers (VPS) hosted by OVHCloud and Centrilogic, bypassed SPF (Sender Policy Framework) controls because the SPF records configured by Proofpoint were too tolerant in case of sending from Office 365 accounts. Access to a Proofpoint relay server was possible through any account. This configuration allowed criminals to abuse such accounts and forward emails through Proofpoint’s service.
Source: Guardio Labs
Additionally, the way Proofpoint’s DKIM (DomainKeys Identified Mail) settings had been configured ensured that the emails were properly signed, contributing to their alleged legitimacy. As a result, major platforms like Gmail didn’t identify the emails as spam, for example.
Source: Guardio Labs
Proofpoint put together a guide containing advice on setting up more stringent anti-spoof measures. The company also offered assistance to companies on how to better secure their accounts. Despite notifying Microsoft that compromised Office 365 accounts were active, some have been in use for more than seven months.
