
Security

Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
Timeline

Cisco discloses high-severity IP phone vulnerability
The vulnerability impacts Cisco's IP Phone 8800 Series and IP Phone 7800 Series devices. The bug, tracked ...

Employer services company Sequoia suffers personal data breach
A data breach at Sequoia has resulted in personal information being exposed. Sequoia lost customers' sensi...

Palo Alto Networks launches Cortex Xpanse Active ASM
Cortex Xpanse Active ASM is generally available. The solution helps find and resolve vulnerabilities in inter...

Ransomware group Play threatens to publish Antwerp’s data
Ransomware group Play claims to hold 557GB of data from the city of Antwerp. The local government fell victim...

Beyond Identity launches zero trust integrations with Zscaler
Beyond Identity introduced several new integrations with Zscaler's solutions. The MFA vendor aims to expand i...

Ransomware hits Rackspace Hosted Exchange
Rackspace announced that the recent Hosted Exchange outage was due to a ransomware attack. The service is sti...

Hackers hijack Linux devices using PRoot-isolated file systems
Hackers are using BYOF (bring your own filesystem) attacks to abuse the open-source Linux PRoot utility and d...

‘Zero trust high on agenda due to cloud, potential untapped’
The security world has been under the spell of zero trust for some time. Zscaler research now confirms that o...

Ransomware hits city of Antwerp
Cybercriminals infected the city's IT systems with ransomware. Residents are unable to make appointments for ...
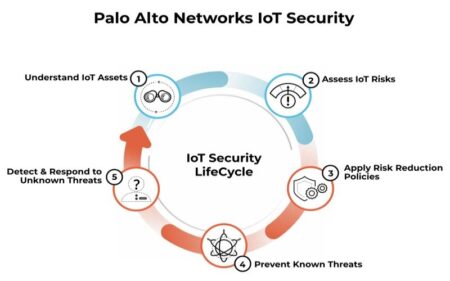
Palo Alto Networks releases Medical IoT Security
Palo Alto Networks introduced Medical IoT Security, a zero-trust solution that secures connected medical devi...