
Wiz sees big impact of AI on runtime security, but also stresses old threats
Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...

Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.

Sophos announced on Thursday that it is acquiring Braintrace, a startup with technology that detects maliciou...

The innovation would allow banks to remove limits on contactless payments. This week Paris-based Thales an...

CloudKnox Security, a startup with venture capital funding, is being bought by Microsoft. The software giant ...

Google has released Chrome version 92, with several fixes for highly severe flaws and new privacy features. C...

A group of hackers backed by the Chinese government may be expanding from state based targets to go after the...

Google's 'invisible security' plan is advancing after the company released several updates for its existing s...

Systemd, the Linux system and service manager, has become more prevalent than init as a Linux startup and con...

Rapid7, the security automation technology firm, announced that it will pay $335 million in cash and stock to...

Amazon Web Services has shut down cloud infrastructure and accounts linked to the Israeli-based NSO group acc...
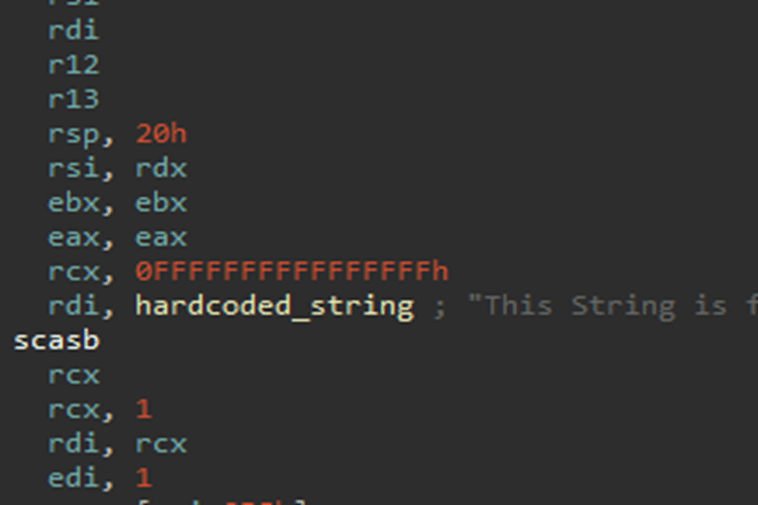
SentinelOne recently uncovered a vulnerability in HP and Samsung printers. This is a so-called escalation of ...