More integrations between different parts of Cisco’s extensive portfolio in networking and security, combined with as-a-service consumption models meant to make customers’ lives a lot easier.
For years, Cisco events were mainly about adding new features, products, services and often entire acquired companies to the portfolio. This has resulted in an extensive and very powerful platform that you can use in any way you want as an organization. One consequence of this was that the portfolio could appear rather complex and confusing. The hybrid world organizations are moving towards add even more complexity. Organizations have moved towards a distributed and hybrid infrastructure, not to mention the impact that hybrid working has on their IT environments.
So some of the complexity has been created by Cisco itself, some is the result of general market developments. The good news from Cisco is that because of the important role it plays in these developments, the company can therefore also help solve them. Chuck Robbins, Cisco’s CEO, promises to do just that during the keynote: “We want to simplify the things we do with customers. We’re working hard on that, and we’ve made some good strides in doing so.” He is also refreshingly honest when he points out that while Cisco has made some progress, it really needs to improve. Among other things, he mentions simplifying licensing and merging the various platforms that Cisco has on offer.
Meraki and Catalyst merge
One of the ways in which Cisco wants to simplify things is by linking platforms together. According to Todd Nightingale, the EVP for Enterprise Networking & Cloud of the company, Cisco has put the burden of the complexity of multiple platforms existing side by side on the customer for too long. He says the company is now seeing the impact of that with these customers. The IT experience is too complex, and that ultimately means the end-user experience suffers as well. In an interview with us, Nightingale qualifies this statement a bit further, when he says that it wasn’t only Cisco that was to ‘blame for this. It was how the industry as a whole worked. This resulted in tremendous progress, he states. However, the industry more or less forgot about the impact on customers in terms of user experience.
To counter the negative side effects of more than a decade of progress, Nightingale (and Cisco) made a big announcement during Cisco Live. In fact, it was the biggest announcement of Cisco Live. Not the most surprising by the way, because it was inevitably coming, but a very important one. Cisco is going to merge Meraki and Catalyst. That is, it will ensure that Catalyst products can be managed and monitored from Meraki’s cloud platform. In doing so, Cisco says it is merging the number one cloud-managed networking platform with the number one campus networking platform.
Mind you, it doesn’t mean that the current ways to manage and connect Catalyst hardware will be retired. There will still be support for Catalyst hardware from (on-premises) DNA Center. Customers and partners can also continue to use CLI to do the management. Lastly, all Catalyst hardware that has come to market since the introduction of the Catalyst 9000 series can become part of the new management environment.
Is this merger good news for everyone?
Merging Meraki and Catalyst may be a good and timely move on paper. However, what does it mean in practice? Also, how will the market react to this merger? It’s not hard to imagine that not everyone will be happy with this. Partners and organizations have been using Catalyst for a long time now. Changing how they monitor and manage that platform is quite fundamental. We wouldn’t be surprised if many of them want to continue to use Catalyst hardware in the old way.
There are several reasons for this. The first is that until at least a few years ago, Meraki had an SMB/SME focus at Cisco as far as we know. As such, the Enterprise Networking division and the Meraki division are two different parts of the company. That must affect the capabilities that Meraki offers versus what Catalyst offered and is offering. The second reason is that many partners have created a business model around the ‘complex’ nature of Catalyst management. They don’t want to give that up.
In time, these two parts will undoubtedly move (even further) towards each other. This will not be the case immediately at launch. In any event, Cisco will be more in the driver’s seat moving forward, according to Nightingale. That is, the new offering won’t be about having as many features as possible anymore. “We don’t necessarily want to try to be feature-complete, but use-case complete”, he states. This probably means that the number of features will decrease. Nightingale more or less confirms that. He gives a (hypothetical) example that the new environment may well reduce the way you do a specific configuration from twelve ways to two ways.
Mind you, reducing features, specs and options is not necessarily a bad idea. In fact, it’s where the market as a whole is headed. We are moving more and more towards a self-driving, autonomous network, in which AI will play an increasingly important role. That no longer includes extremely complex manual configurations. Whether all current Cisco customers and partners who use Catalyst hardware already think this way, however, we wonder. That may take some time. Cisco has quite a lot of legacy there (in the positive sense of the word). As far as we are concerned, however, Cisco has taken the right step by merging the two environments. It is now up to the company to convince customers and partners of its added value.
Making everything available as a service
Merging Meraki and Catalyst is about reducing complexity in Cisco’s own portfolio. In addition to this, the company also announced something today that should address more general complexity. More specifically, complexity caused by the move towards a hybrid infrastructure. To address this, Cisco announces the Nexus Cloud SaaS offering. This will allow customers to manage their Nexus devices in their data centers from the cloud. Nexus Cloud is part of (or powered by) the Intersight Platform. Intersight is a collection of services that allows organizations to deploy and optimize their distributed infrastructure, among other things. Intersight sees all the endpoints in the infrastructure and analyzes the telemetry data they generate. Additionally, there are services within Intersight that deal with optimizing Kubernetes environments and HashiCorp Terraform environments.
Adding the management of Nexus devices into organizations’ private cloud should obviously simplify and speed up things like deployment and management (think upgrades) of infrastructure a lot. It also integrates with the other services within Intersight. That means you can now manage UCS servers, HyperFlex HCI, Nexus-based private clouds, cloud-native Kubernetes environments and third-party hardware from a single location. This should bring the promised simplification another step closer for customers.
The introduction of Nexus Cloud, by the way, is not a standalone event, according to Robbins. “Everything that we can deliver as a service, we want to start delivering as a service,” he stated during his keynote at Cisco Live. As was the case with the integration of Meraki and Catalyst, the “old” way will continue to be available as well. That is, if you don’t want to use Nexus Cloud, you don’t have to.
Distributed environments require further integration and simplification
When we talk about making it easier to set up and deploy infrastructure, you can’t ignore security. Especially in a hybrid and distributed architecture, it can quickly become a confusing topic. Jeetu Patel, the EVP Security and Collaboration at Cisco, sees this as a golden opportunity for Cisco. This is because Cisco focuses on a platform approach to security. That approach entails deep integrations between different components within the portfolio. “The complexity of hybrid architectures and the increasingly sophisticated threats lead to a preference for an integrated approach to security,” he states.
Providing integration between different components alone is not enough to get the desired simplicity. From Cisco’s point of view, there is also a fair amount of work to be done to make the experience as a whole as good as possible. That starts with something as simple as merging all the different clients into a single client or application. Now Cisco offers a VPN client, a client for DUO and about twenty more. “We really need to get away from that,” Patel indicates. So we will see a consolidation of all those security clients into one.
Simplicity is leading in development of new products/services
Solving the complexity of the past is part of Cisco’s ambition. However, this also has consequences during the development of new products and services. These must be as simple as possible from the outset, without losing any of their capabilities.
An example of such a new product is Cisco+ Secure Connect. This is (part of) the company’s SASE solution. “It’s completely turnkey and therefore easy to use,” says Patel. Cisco’s SASE offering also scales very well, with Points of Presence around the world. In addition to pre-login security, Cisco also doesn’t forget about post-login security. That’s why it developed Wi-Fi Fingerprint. This new feature makes it possible to offer continuous trusted access. The interesting thing about this feature is that it does not reveal where you are geographically, because that is undesirable. It scans the SSIDs in the area and thus determines whether an employee is in an environment where he or she can access the company network and resources with full privileges or not.
The cloud also plays an important role for Cisco in the area of security. During his keynote, Patel talked about, among other things, a firewall management center as a SaaS solution. This allows you to manage on-prem and cloud firewalls from a single location in the cloud.
All in all, Cisco wants to provide an end-to-end platform solution for prevention, detection, response and threat intelligence. The management of that platform must happen at a central location too. For that, Cisco seems to select the cloud.
Finally, there is the issue of lock-in. A vendor like Cisco has a very extensive portfolio. That immediately conjures up images of vendor lock-in. That may have been the case in the past, but has changed in recent years. The fact that Cisco uses OpenAPI standards is an example of this. So you don’t have to buy everything from Cisco, and still have deep integrations with third-party tooling.
Integrating WAN and SD-WAN with ThousandEyes WAN Insights
A final example of integration within Cisco and thus of simplifying offerings and reducing complexity is ThousandEyes WAN Insights. With Cisco’s acquisition of ThousandEyes a few years ago, Cisco acquired new WAN capabilities. One of those capabilities is ThousandEyes WAN Insights, which Cisco announced during Cisco Live. This is an integration between ThousandEyes’ offering and Cisco’s SD-WAN offering. In other words, it links the configurations of WAN connections to cloud services and other sites to the insights ThousandEyes has around the quality of the global backbone.
The idea behind ThousandEyes WAN Insights is that it is becoming increasingly important but also increasingly complex to optimally configure connections across the WAN. With this new offering, ThousandEyes continuously analyzes so-called path metrics from Cisco vAnalytics. Based on that, ThousandEyes WAN Insights provides recommendations back to Cisco SD-WAN to optimally route outbound traffic.
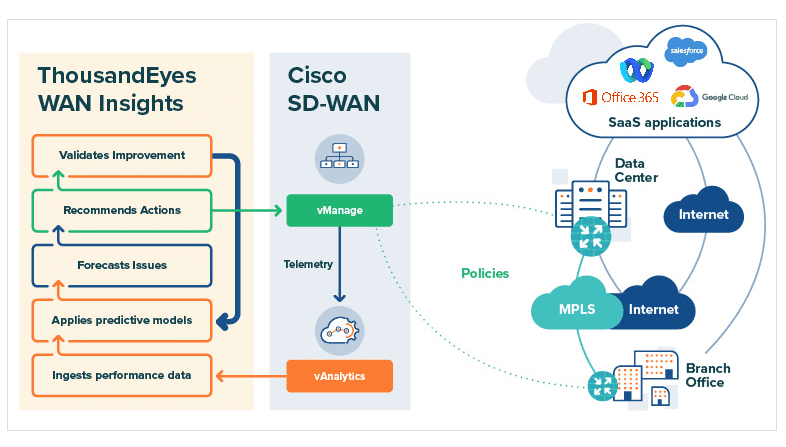
So ThousandEyes WAN Insights is about analyzing each individual path, not merely the connection between sites as a whole. In practice, there are often several such paths per connection. These often run via different networks, such as a provider’s fiber optic network and MPLS. According to the ThousandEyes WAN Insights announcement, it needs an average of at least 24 hours to gather the data it needs to make recommendations.
At the end of the day, the outcome of ThousandEyes WAN Insights should be that applications/environments such as Webex, Salesforce, Office 365 and Google Cloud perform better and that connections between branch offices and a data center have a higher availability and perform better.
More generally, according to Cisco, ThousandEyes WAN Insights allows you to move from a reactive to a proactive attitude. You no longer solve problems after they occur and your organization is therefore affected by them, but before this is the case. As far as we understand it, there is no automation yet of the steps to be taken to fix the upcoming problem. That is, ITOps teams need to get to work with the input from ThousandEyes. Toward the future, it should become possible to automate that step.
Conclusion
The announcements and strategy discussed in this article shows that Cisco takes its role as a major player in the IT and security industry seriously. It has to as well, by the way, otherwise it will lose that role. It is good to see that Cisco looks critically at its own offering too. Addressing the complexity of the current landscape starts with reducing complexity in its own offering. Not everyone will be happy with the changes. Then again, that always happens when you fundamentally change things.
Mind you, merging Meraki and Catalyst is also simply necessary in order to keep up with the other players. Enterprise networking is inexorably on the way to being cloud-managed. That’s the way it is nowadays. We are curious to see whether Meraki can carry and propagate the Catalyst legacy (in the positive sense of the word) from the cloud. In any case, Cisco will have to work hard to demonstrate the added value of this. It will certainly do so, if we are to believe Nightingale: “We are going to make it so convincing that customers will want to make the switch themselves.” That’s a nice promise, one we’ll keep in mind. We’ll be sure to come back to it in subsequent conversations with people at Cisco, too.
