Phishing is an Internet scam tactic dating back almost as far as email itself. It still accounts for a hefty 80% of all cyber attacks. Research by cybersecurity specialist Sygnia shows what a sophisticated phishing campaign can look like.
We’ve been intimately familiar with Sygnia’s work for some time. The Israeli company managed to unravel the practices of the cybercrime group RagnarLocker and offered valuable insights in our roundup of the Log4Shell vulnerability. Earlier this year, Sygnia’s IR (incident response) team helped a customer that had fallen victim to a BEC (business email compromise). In other words, they had fallen for a convincing-looking email that turned out to be malicious.
The perpetrators mimicked a trusted file-sharing service and an Office365 login page that was difficult to distinguish from the genuine article. Furthermore, the security slip-up was not simply negligence on the part of an individual employee: in fact, the email came from an outside party that the company in question did business with, who had presumably already been compromised. In short, this could happen to anyone.
Uniform approach
Sygnia’s blog post describes the steps the attackers took to fool victims. The most striking details pertain to the convincing-looking emails and login pages, which can be seen below:
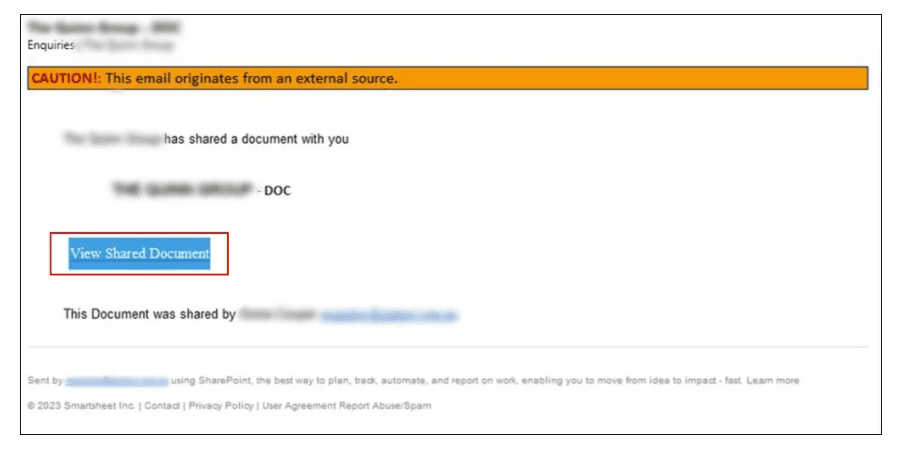
This type of scam differs from many phishing attempts that experienced users will recognise immediately. The example cited by Sygnia clearly involves a group of attackers who know how to get their targets to hand over their data. To make matters worse, there was an “I’m not a robot” checkbox that seemed to lend additional authenticity to the fraudulent pages. This was only advantageous to the threat actors, allowing them to disguise their identity further.
The idea behind it all was that the victim entered legitimate login data into the fraudulent webpage, which meant the attackers had already acquired valuable information. However, this was only the start of it. The hijacking of MFA (multi-factor authentication) permissions was also of crucial importance, so that an external device could provide authentication and provide persistent access. This was accomplished by robbing the session tokens of the device in question.
Once a victim’s account was accessed, the group took steps to do even more damage. Not only was the data of the user in question compromised, but it also became an attack vector for later attacks. After all, the criminals repeatedly used newly obtained accounts for further distribution, complete with fraudulent URLs that resembled the domain names of the companies in question.
On the trail
The group was not wholly unknown, the Sygnia investigation revealed. It was already reported on VirusTotal that the compositseone[.]com domain used by this party had already been flagged by 8 security parties as being used for malicious purposes.
Sygnia used multiple tools to determine which companies had been attacked and how the tactics differed. It turned out to be dozens of organizations worldwide, with the attackers not adjusting their email tactics. File-sharing was the false pretext used to trick users; something made extra risky by the fact that it had already compromised trusted partner companies. Thus, attacks jumped from company to company based on the mutual trust between these parties.
Still growing
The fact that email scams have been around for so long makes it logical to assume that we are getting fooled by them less often than before. Nothing could be further from the truth, unfortunately. Sygnia cites the FBI, as it described BEC (business email compromise) as one of the largest and most damaging Internet crimes in its 2022 report.
Sygnia hopes to quell this threat by not only hunting down such groups on its own, but it’s also sharing how it came to discover them. It is up to others to take advantage of this. For the ordinary employee, the key is to always be on guard against deception. Yet this case proves it is insidiously easy to be led astray by malicious parties.
What is possible?
One can think of several explanations for the continued popularity of phishing. Yet two stand out: the fact that no malware is required and its rapid spread. Phishing relies on persuasion, unlike a piece of code that can slip into an IT environment through a software vulnerability. Those who lie convincingly and have a knack for mimicking a legitimate service can fire hundreds of emails toward potentially lucrative targets. If there is even one victim, it already presents an opportunity to operate from a new source.
In addition, there is no doubt that email scams can adapt to present-day trends. For example, Palo Alto research recently revealed that malicious actors are capitalizing on the current AI hype by cloaking scams in AI-related language and links.
The objectives for doing so vary. Compromising an important account can already have major consequences through a data breach. However, there is much more to be done with stolen credentials, especially if they have bypassed MFA. Consider the selling of login data, as happened with Genesis Market.
In other words, phishing offers many opportunities. We haven’t even mentioned the classic phishing style, which experienced users can quickly recognize, but which preys on the least digitally savvy individuals among us. Ultimately, parties like Sygnia will continue to be necessary to recognize when a group of criminals comes up with another new tactic affecting many organizations.