Medium-sized companies are often popular targets for cybercriminals. The security of these organisations is not always at the right level, allowing hackers to break in and cause significant damage with relative ease. However, with a good approach and strategy, the risks can be limited
‘The question is not if, but when you get hacked’ is a popular statement within the cybersecurity landscape. With cybercriminals becoming increasingly innovative and committing more sophisticated attacks, the message is highly relevant. Both global and smaller players are being victimised.
Many of the successful cyberattacks can potentially be repelled, Dell Technologies observes. Medium-sized companies with a few hundred employees, where the necessary resources and knowledge are not always present, can also become more resilient. As doing too little is not an option given the current threat landscape, the right help is desirable.
Few changes, different emphasis
Secureworks (majority-owned by Dell Technologies) wanted to get perspective on the current threat landscape and protection for mid-sized businesses. According to a 2021 study, little changes in the year by year outline. For example, ransomware has been the biggest threat to organisations for years. On top of that, Secureworks confirms that attacks are becoming more sophisticated and extensive. Whereas a successful attack years ago only blocked a few devices in an organisation, attackers now regularly take the time to infiltrate the IT infrastructure and gain control before applying encryption. It forces companies to negotiate with cybercriminals.
According to Secureworks, the number of zero-day vulnerabilities has also been increasing recently. It is estimated that 20 percent of hacks occur because a software vulnerability is discovered by cybercriminals before the vendor. There’s not much you can do about this as a software user, because there are simply no patches available for such attacks. At the same time, it means that some 80 percent of attacks are still performed in the traditional way, with traditional tools.
Another major threat for medium-sized companies is Business Email Compromise (BEC) attacks. For example, fake emails are sent, supposedly from a director or an important partner, to commit financial fraud. Secureworks recommends that everything concerning identity should be properly regulated due to the increase in such attacks. “Make sure that the identity integrity of devices and users is secured”, said Enterprise Account Executive Philip Hebly during a cybersecurity webinar organised by Dell Technologies in partnership with Intel.
How are mid-sized businesses handling security?
With these significant threats, the question of how the average company with a few hundred employees handles security remains. Through an answer, you can compare your company’s profile to the market. Most organisations see the continuity of production and business processes as the biggest threat. That’s where they absolutely want to avoid damage as a result of an attack. A logical thought, as production and business processes are what a company runs on and exists for. Customer data and personal data are also seen as significant risks, although Secureworks connects the latter with the risk of production and business processes. After all, all of these domains are compromised when a company becomes a victim of ransomware and data loss.
If we look at how companies determine their approach and strategy concerning security, there are some differences. For example, 45 percent indicate that they determine their policy based on proprietary research and insight. The same group does this based on security tests and assessments. However, there are also frameworks available that have security built into them, such as CIS, NIST and SANS. Despite this, only 10 percent determine their approach and strategy based on these frameworks.
The Secureworks survey also finds that most organisations believe they are more secure than other mid-sized companies. They generally use and deploy next-gen firewalls, Endpoint Detection & Response (EDR), and additional network and cloud security solutions. Yet only a small proportion actively monitors security incidents, which is somewhat concerning.
Protection at the front end
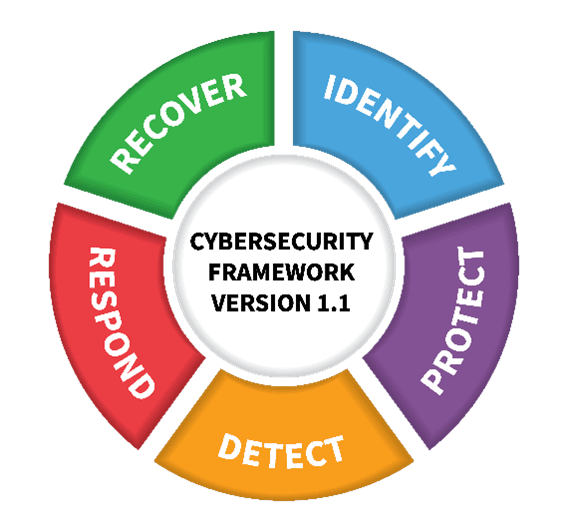
In an ideal world, companies would prioritise security, making themselves a more challenging and thus less attractive target to hack. During the webinar organised in collaboration with Intel, Dell Technologies repeatedly mentioned the NIST framework as a guideline, including the necessary steps regarding identification, protection, detection and response. In other words, you build in the required protection and response capabilities at the front end of your organisation. According to the tech giant, if you pay attention to that, you are well on your way to secure infrastructure, while the data and end users in that infrastructure are also relatively secure.
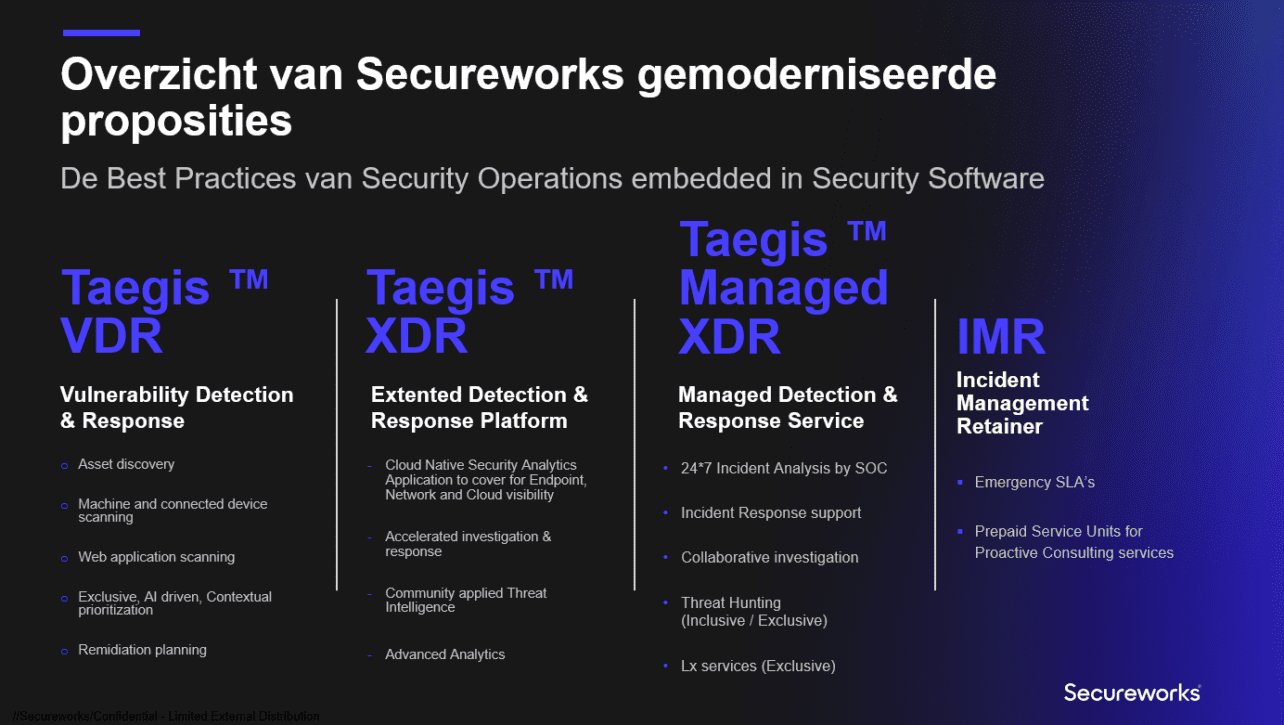
With Secureworks, Dell Technologies has the capabilities of getting things done, particularly on the detection and response side. With the Detection & Response Platform, everything in the infrastructure is monitored. That means keeping an eye on what is happening on endpoints, network environments, and cloud infrastructure. If there are any vulnerabilities, the platform helps resolve them. A Security Operations Center is constantly watching so that, in the event of an attack or abnormal behaviour, help is available. The security risks are thus significantly reduced, as the deployed functionalities in the image below shows.
Of course, when we look at the complete portfolio, Dell Technologies’ security capabilities extend beyond Secureworks. While the subsidiary plays a prominent role, the tech giant also looks at specific security features for its endpoint and IT infrastructure solutions, among others. It also recommends other ‘front end measures’, such as antivirus and firewalls.
What if you are hacked?
As a medium-sized company, taking the above measures means you are on your way to a proper defensive wall. However, it does not offer a 100 percent guarantee. Therefore, the NIST framework also recommends a focus on recovery. That way, if all the built-in measures are circumvented, you will still be able to resume production and business processes as quickly as possible and have the correct data at your disposal again. After all, you want to be offline for as short a time as possible.
That’s why the tech giant has been looking for an approach that is a little less dependent on the way data centres are traditionally set up. Data centres normally house both the production, disaster recovery and backup environment. If any segment is hacked, all segments are at risk. This means that the last resort — backups — is often affected as well, making recovery all the more difficult.
The answer: the Cyber Recovery Vault. This vault is invisible to the production environment, backup systems and software. The Cyber Recovery Vault initiates a connection via an operational air gap to retrieve backup data from the vault. It opens and closes the connection to the vault through an automated process. After that connection is established, the backup data is pulled out, and the connection is closed. The backup data copy is also immutable, which means that the data can no longer be accessed after it has been written. The vault also checks for ransomware in the backup, so that when it is restored, the wrong files are not brought in. It should guarantee that data is always clean. According to the tech giant, the Cyber Recovery Vault leverages a containerised connection protocol to make it extremely difficult for hackers to hitch a ride. “Through direct connections between devices, they can’t even see activity”, the company says.
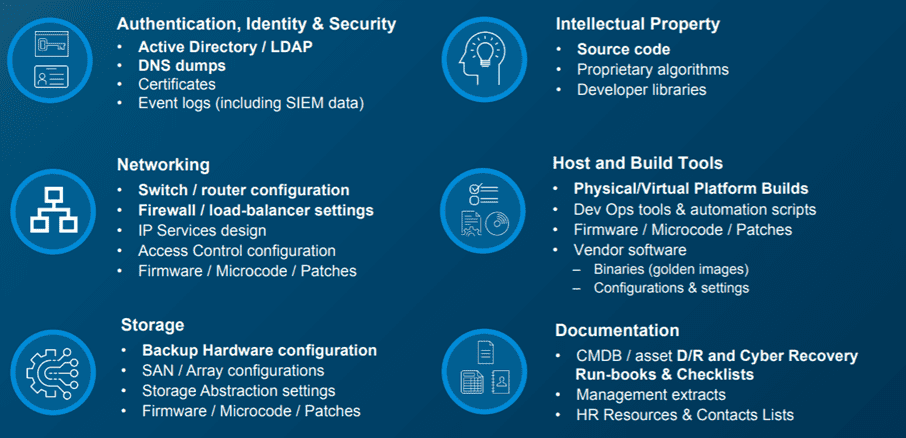
The tech giant notes that The Cyber Recovery Vault can be useful when, for example, all data has been wiped from the production environment. Therefore, it recommends putting the most critical data — ‘the crown jewels’ — in the vault. In the image below, you’ll find data that is potentially interesting as a copy in the Cyber Recovery Vault.
Affordability and feasibility
Ultimately, it makes sense to invest in making your organisation safer. Especially since the damage can be incalculable when your company becomes a victim. Ransom demands can amount to hundreds of thousands, even millions of euros, not including consequential damage. If your business processes are shut down for days, the collateral damage is going to be high.
However, the financial resources and knowledge to invest in security can sometimes be lacking. During the webinar, held in collaboration with Intel, it was also discussed how you can apply for subsidies for digitalisation and make your organisation more resistant to attacks. After all, governments have just as much stake in secure organisations as organisations themselves. Applying for said subsidies removes another barrier to investing in cybersecurity, at a time when the risks are constantly increasing.
Are you curious about the webinar of Dell Technologies in collaboration with Intel? You can watch the recording back via this link.