
Why did so many security vendors abandon MITRE’s stresstest?
This year, MITRE made headlines primarily because its leading vulnerability database was in danger of being d...

This year, MITRE made headlines primarily because its leading vulnerability database was in danger of being d...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.

Security Datalake is taking on an increasingly central role in SentinelOne's offerings. XDR and the new Purpl...

Ivanti recently patched as many as fourteen critical security vulnerabilities in its enterprise MDM solution ...

A new phishing method aims to sidestep the two-step verification of Instagram accounts. A misleading email me...
A new type of attack is targeting the Secure Socket Shell (SSH). This network protocol is used for data trans...

A new form of e-mail spoofing was revealed this week: "SMTP Smuggling." The vulnerability allows threat actor...
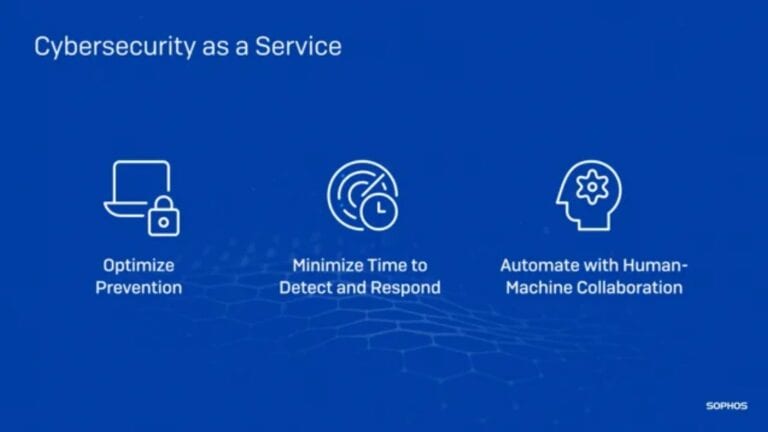
With cybersecurity-as-a-service (CSaaS), Sophos aims to protect companies from growing and evolving cyber thr...

Okta recently acquired Israeli start-up Spera Cybersecurity for between $100 million and $130 million. With t...

Major ransomware groups are increasingly using remote encryption in their attacks. Also called remote ransomw...

The U.S. Department of Justice has released a decryption tool to combat the effects from the infamous ALPHV/B...

MongoDB is still investigating a security incident in which hackers penetrated customers' business systems. C...