Every year, Sonatype takes a good look at the software supply chain. In this year’s State of the Software Supply Chain report, researchers report that many more malicious packages have been discovered than before. At the same time, a version with a fix is almost always available. Sonatype also found that respondents overestimated the security of their own software packages.
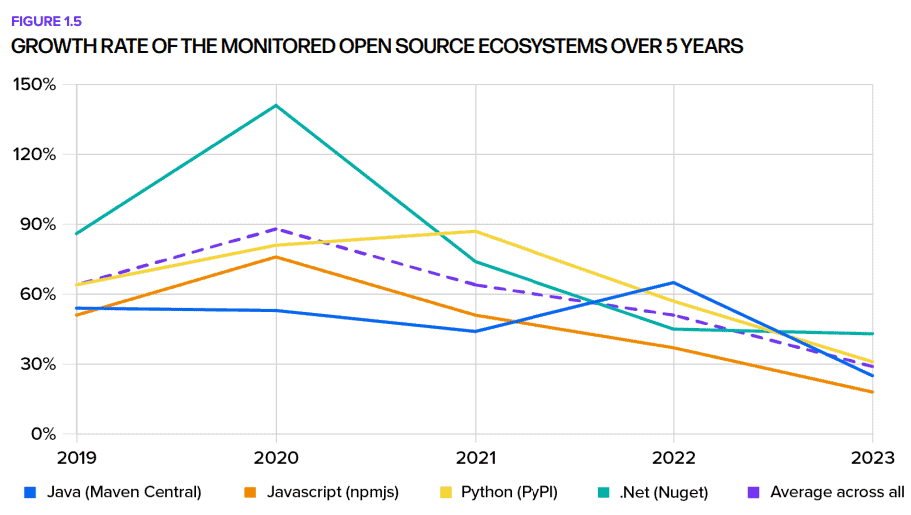
To map the open-source supply chain, Sonatype looked at the four most popular open-source ecosystems: Java (Maven), JavaScript (npm), Python (PyPI) and .NET (NuGet Gallery). Overall, Sonatype sees a steady recovery in the open-source supply chain among these programming languages. Before Covid-19, its adoption rate was significantly faster, but nowadays, it’s growing at a relatively stable 15 percent year-over-year. The dip seen during the pandemic can be explained by reduced productivity in the IT and communications sector until 2022, according to Sonatype. Another factor may be that there are actually more commercial entities involved in open-source software than previously thought. In any case, the consumption of open-source components is still on an upward trajectory, but the rate of growth is decelerating. This may be a sign that the market is becoming saturated.
One thing that’s increased tremendously is the amount of malignant packages discovered: 245,032 between January and September 2023. The researchers note that this is twice as many as in all previous years combined. It’s an indication of the explosion in the use of the supply chain as an attack vector. In addition, nation-states (such as North Korea through the Lazarus Group) are increasingly targeting the supply chain.
Insecure versions (including still from Log4j)
The Sonatype report cites that software developers often lack the time required to do their jobs properly. That is to say, they have an enormous task just figuring out if a piece of software is in any way vulnerable, be it directly or indirectly through dependencies. To illustrate, the average Java application has 148 dependencies and 10 annual releases. A developer therefore has to keep track of an average of 1,500 dependency changes and evaluate them in terms of security level. “Now imagine the scale of these decisions for companies with tens of thousands of developers and thousands of applications,” the Sonatype researchers remark. It’s a further sign that supply chain incidents will become increasingly common.
This has the unfortunate consequence that the vast majority (96 percent) of vulnerable software being installed, already has a secure version available. Compounding the issue, survey participants also falsely believe themselves to be safe: 67 percent are confident that they’re not reliant on vulnerable libraries, even though 10 percent of all respondents say they have been attacked via open-source vulnerabilities in the past year.
Some security incidents have reached global notoriety, but even then, mistakes are still being made. For example, a quarter of all Log4j downloads this September still involved a version that did not contain a patch for the globally impactful Log4Shell vulnerability.
Tip: Log4Shell in 2023: big impact still reverberates
New policy: scorecards
With each annual Sonatype report, the researchers do a deep dive into a specific subject matter. In this case, they looked at the state of affairs regarding security scorecards. At first glance, a company may be using secure software, but through dependencies within an organization’s software package, there are still unseen vulnerabilities.
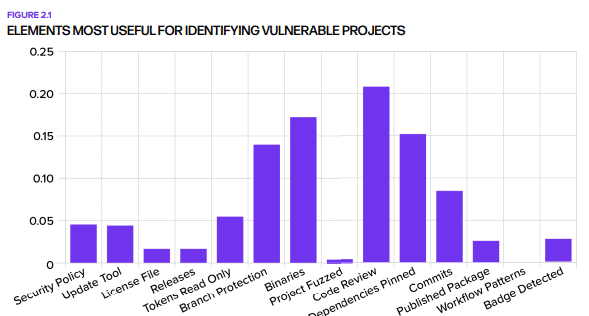
To assess the security of open-source software, Sonatype lists a number of checks. Most important of all is Code Review, which refers to peer-reviewing other contributors’ work when it comes to code changes. Likewise, Branch Protection ensures that there’s a review process preceding the pushing of new code. Unfortunately, these practices are rarely followed, nor has there been a general improvement in the adoption of best practices. In addition, open-source consumers should keep checking that software is still actively being worked on: 18.6 percent of all previously active projects stopped being maintained over the last year.
Software Bill of Materials in demand
Governments haven’t been sitting still, either. U.S. guidelines around cybersecurity have been tightened, while the EU has tabled the Cyber Resilience Act, among others. Aside from the headaches this creates for open-source developers, it also forces organizations to look more closely at the software they run. Sonatype has spotted a rising demand for Software Bill of Materials (SBOM), which provides an overview of all the components that make up the software in question. As a result, it’s up to vendors to be able to reassure consumers about their cyber hygiene.
The researchers note that keeping track of an SBOM alone does not equate to better security. Still, it helps build a secure and reliable software marketplace, they suggest. 53 percent of the engineering professionals Sonatype researched, generate an SBOM for each application. This subset of those surveyed also reports fewer security incidents than their colleagues who do not maintain an SBOM. SBOMs are even more popular among security personnel at large companies, where 75 percent construct them for each application. Nearly half of this group has started asking vendors for SBOMs for purchased software.
As positive as these signs are, it appears that cyber-attackers are still given far too much time to do their dirty work. 39 percent of respondents only fix a vulnerability after a week, later or never. Since hackers primarily work with automated scanners to detect vulnerabilities, many organizations are thus an easy target for an unnecessarily long time.
