There are a lot of AWS S3 storage buckets that can expose their stored data at any moment due to misconfiguration, according to an investigation by Truffle Security.
AWS S3 storage buckets are a common way of storing files in AWS. The buckets can be viewed online by anyone with no prior authentication. Although this is useful for public access, it also creates a security risk. Especially if these files contain sensitive data such as passwords, security keys and API keys. According to the experts of security specialist Truffle Security, this means that the possibility of an incident is never far away.
Unsecured AS S3 buckets
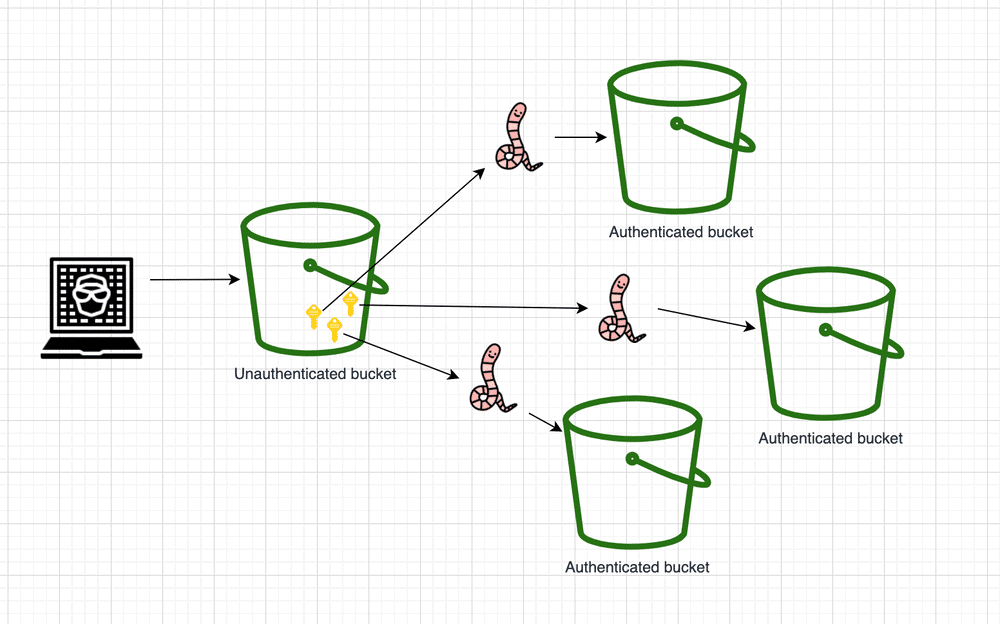
In a recent study, experts from Truffle Security discovered that data leaks with AWS S3 buckets are very common. They discovered more than 4.000 unprotected S3 storage buckets with highly sensitive private data. Within these AWS S3 buckets, they came across an average of 2.5 pieces of ‘secret or sensitive’ data. In some several cases, they discovered as many as 10 pieces of sensitive data. These included SQL Server passwords, Coinbase API keys, Azure Blob and MongoDB credentials.
Possibility of worm attacks
In addition, security experts discovered login details for other AWS buckets that were configured to request access with a password. According to Truffle Security, hackers could use the first set of open S3 buckets to use those keys to launch an attack on other AWS S3 buckets. This makes this type of attack on AWS S3 buckets ‘wormable’. This drastically increases the impact of a data breach.
Truffle Security has since notified the owners of the open AWS S3 buckets containing the sensitive data. In addition, these experts advise companies that are using AWS S3 buckets to monitor them more closely for possible problems.