Security specialist Censys reports that a recent DeadBolt ransomware attack has hit numerous QNAP NAS devices. QNAP released a forced firmware update for affected devices.
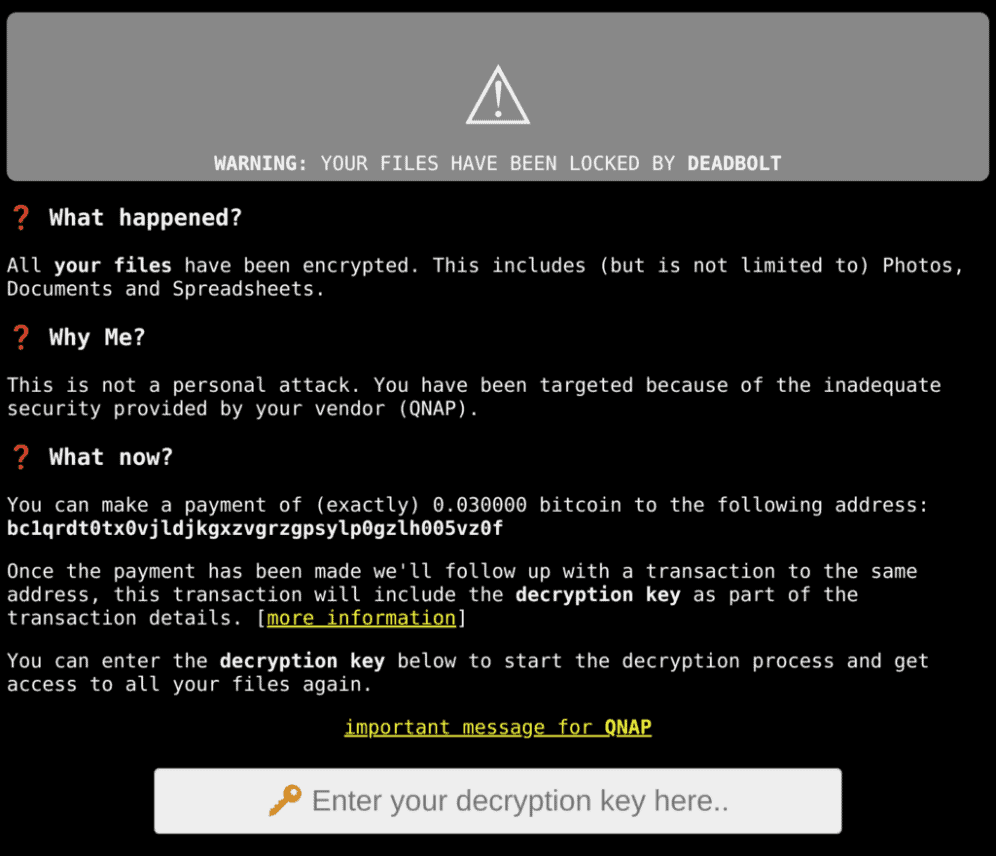
Censys researched 130,000 QNAP NAS devices and found 5,000 units successfully hacked by ransomware attackers. As early as January 25, victims discovered that their data was encrypted and given the .deadbolt extension.
In a message, the hackers stated that victims had to transfer about 1,000 euros (0.03 bitcoin) to obtain decryption keys. The hackers approached QNAP with the offer of a master key for restoring all devices in return for 1.7 million euros (50 bitcoin). It is not known whether QNAP accepted this offer. At the moment, the number of ransomware infections for QNAP NAS devices is steadily decreasing.
QNAP response
In a response, QNAP immediately called on customers to upgrade to the latest version of its operating system for NAS applications. The vendor performed a forced firmware update to apply the latest security patches.
This forced firmware update wasn’t received well by QNAP’s customers. Among other things, users were worried that QNAP devices featured a backdoor. Also, customers that already paid to unlock their files faced problems restoring files following the firmware update. Among other things, this firmware update removes the ransomware executable and decryption interface.
According to QNAP, users were informed of the firmware update’s workings and goals in advance. The vendor says that many users missed the message.
QNAP notes that it’s currently working on a new security update for its NAS products. Customers that set their updates to automatic will receive the update as soon as it’s ready.
Alternative decryptor
Another security provider, Emisoft, released an alternative decryptor for the QNAP hack. The decryptor only works for companies that have already paid for and received a key from their hackers.