Publicly accessible programming code is still often riddled with certain credentials that can give anyone a peek into underlying databases or (cloud) services. This is what security specialist GitGuardian recently found in a survey of 450,000 Python projects.
Developers still cannot keep their code clean of credentials. Too often, this data, such as cryptographic keys, security code and passwords, are still too often housed directly in the written source code.
This can lead to major security incidents where hackers can capture a lot of sensitive data, with dire consequences.
57,000 code-accessible secrets
Research by security specialist GitGuardian into the presence of secrets in the (source) code of Python projects reveals that programmers and developers are indecisive.
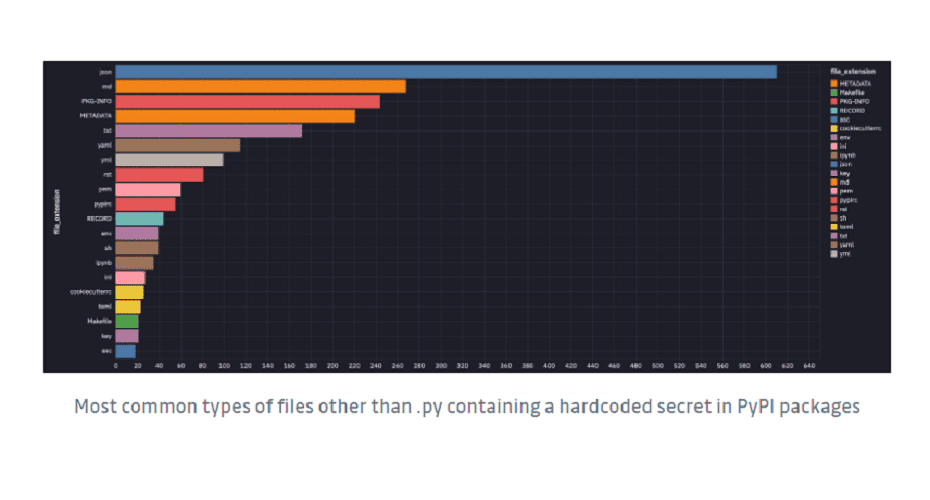
In the 450,000 Python projects examined in the official Python code repository Python Package Index (PyPi), a total of 4,000 built-in secrets were found. About 3,000 projects contained at least one embedded secret. Several secrets were leaked multiple times, bringing the final number to 57,000.
Different credentials found
The credentials the researchers found, gave access to a range of underlying services and servers used to manage business networks. Examples include Azure Active Directory API keys and GitHub OAuth app keys.
Also found were database credentials for MongoDB, MySQL and PostgreSQL, a key for Dropbox, Auth0 keys, SSG secrets, Coinbase secrets and Twilio Master data, among others.
In addition, other database data and tokens for controlling Telegram bots that automate processes for the messaging service were found, the researchers indicated.
After testing all the secrets found, it was found that a total of 786 credentials are still active and can be abused.
Tips for keeping code clean
The researchers provide several tips that programmers can use to prevent their code from still containing secrets. First, they should always avoid using unencrypted credentials. Second, it is important for them to scan their code for such data before releasing it.
Third, they should ensure that credentials stay on their own device and are not distributed to others. Finally, of course, developers can always share their code but not their credentials, GitGuardian points out.
Also read: SAP brings generative AI to developers with Build Code