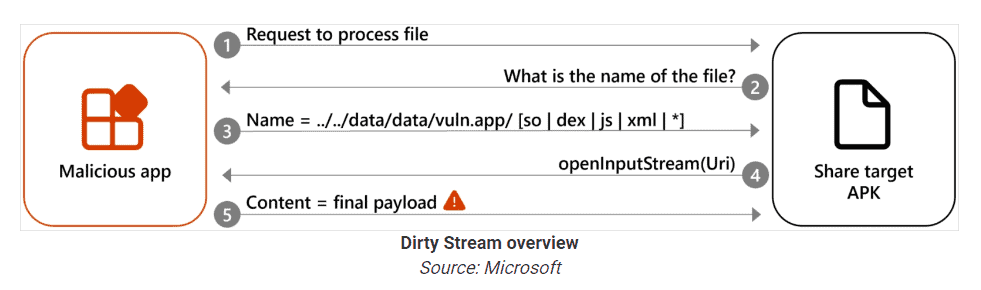
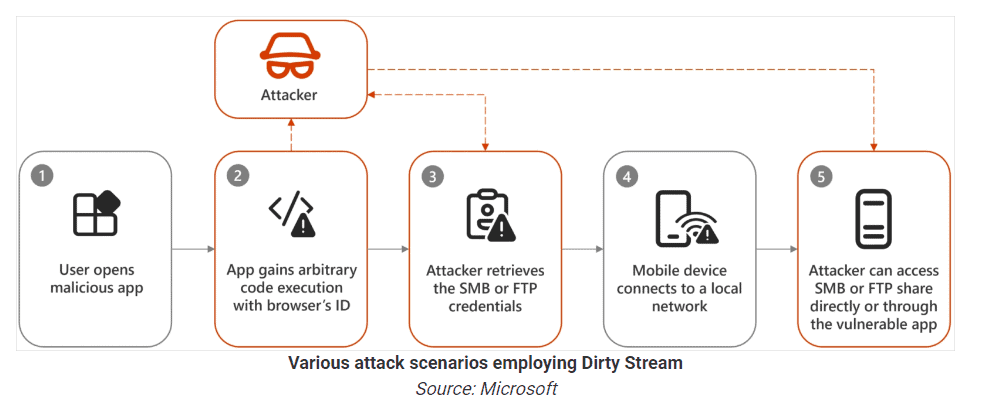
Microsoft has discovered a new attack method that abuses the Android data-sharing feature between apps. This allows malicious apps to overwrite files in the home directory of other apps, thus executing malicious code and stealing data.
According to Microsoft, the cause lies in the improper use of Android’s content provider system. This system manages access to structured data sets intended to be shared between different applications.
In doing so, the system in question provides data isolation, URI permissions and “path validation” security measures to prevent unauthorized access, data leaks and “path traversal” attacks.
If these actions are performed incorrectly, custom intents, the messaging objects that facilitate communication of components between Android apps, could bypass the security measures.
The Dirty Stream attack method capitalizes on this by sending a file with a manipulated file name or path through rogue apps. In the process, the attacked app is tricked into trusting this file or path and executes the file or stores it in a key directory.
Attack surface
According to Microsoft researchers, many Android applications are susceptible to this method of attack, making Dirty Stream a very large attack surface. This would even include applications that have been installed more than 4 billion times.
Well-known named vulnerable applications include Xiaomi’s File Manager and WPS Office.
Also read: Dutch foundation launches mass claim against Google over Android privacy