Hackers are using phishing to mitigate the problems caused by the CrowdStrike update. In particular, attacks to install remote access tools and data wipers are on the rise.
‘Never waste a good crisis,’ many hackers have thought recently. They dived en masse on the recent commotion surrounding the CrowdStrike update bug. According to several security analysts and national cybersecurity authorities, the incident has led to a wave of phishing attacks.
Remote access tool
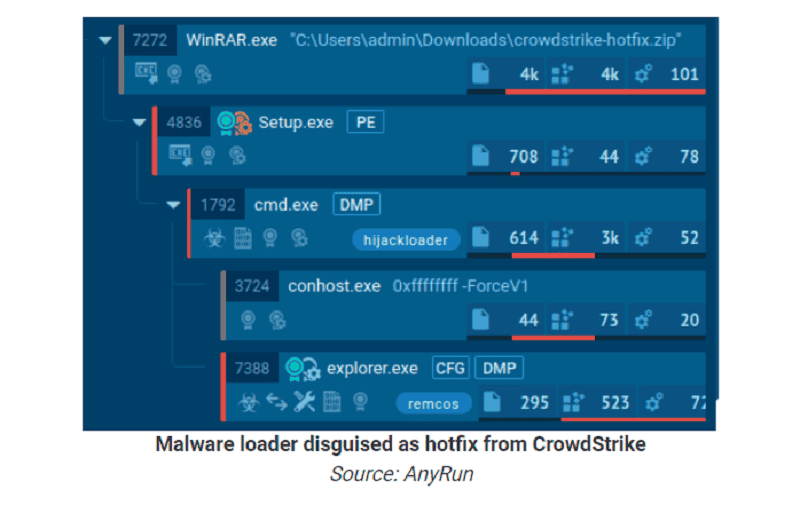
The phishing emails urge companies and individuals to download and install a legitimate-looking hotfix for the problem. In doing so, the hackers pretend that the advice comes from a bank, such as the Spanish bank BBVA.
However, the hotfix is a file manipulated by hackers and installs malware on victims. According to several security analysts, the rogue file installs HijackLoader, which then delivers the Remcos RAT remote access tool to the affected system.
Also data wipers
Fake CrowdStrike hotfixes have also been spotted, indicating that a datawiper is being distributed via these fake updates. Through emails from the domain “crowdstrike.com.vc,” the hackers, likely from Iran, are trying to convince customers to download a tool to fix the CrowdStrike problem.
The emails contain a PDF file with further instructions on performing the fake update and a link for downloading a ZIP file. This ZIP file contains the Crowdstrike.exe file.
When this file is executed, a data wiper is downloaded and immediately goes about its malicious work, overwriting files in the process. The data wiper malware seems to target mostly Israeli companies.
CrowdStrike also warns
CrowdStrike itself also warns of potentially malicious actions by hackers following the update bug. The security specialist has established an official communication channel for troubleshooting purposes, but customers should always verify that they are communicating with a legitimate contact.
CrowdStrike CEO George Kurtz indicated that the blog and technical support are the official channels that distribute updates with information.
Also read: After global CrowdStrike outage, systems restart slowly