A recent vulnerability in Microsoft SharePoint enables an attack on corporate networks. An exploit shows that hackers can gain incremental access to an entire corporate environment after gaining access to a vulnerable SharePoint server.
Rapid7 research shows that a vulnerability in Microsoft SharePoint, CVE-2024-38094, discovered earlier this year, is now being actively exploited. Misuse of this vulnerability can lead to a Remote Code Execution (RCE) attack, allowing lateral access to entire corporate networks.
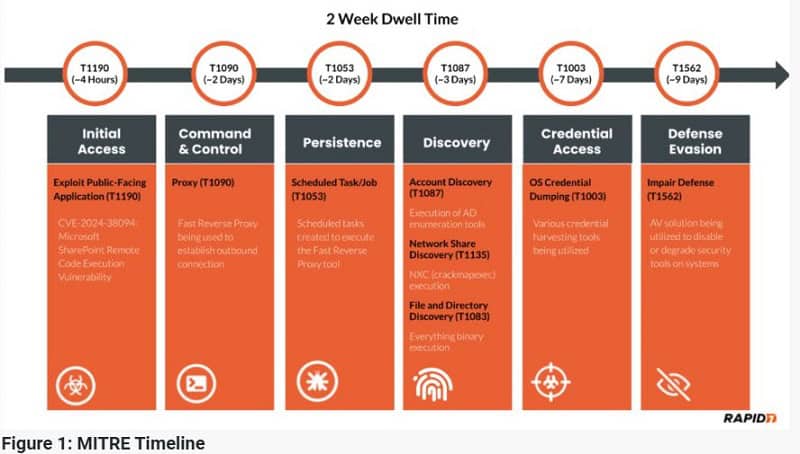
Security experts noted that the vulnerability was exploited via a published proof-of-concept. The hackers managed to hide their presence for two weeks.
Step-by-step attack path
According to Rapid7, the attack path was initially via access to the vulnerable SharePoint server. After this, a Web shell was installed.
After the initial access, the hackers compromised a Microsoft Exchange account with domain privileges, giving them broader access, and installed Horoung Antivirus. This installation caused a conflict that disabled security protections and prevented detection, allowing the hackers to continue operating undisturbed.
The process involved installing the Impacket lateral movement malware and using a Python batch script to install Horoung Antivirus setting up a custom service, executing a driver, and running ‘HRSword.exe’ via a VBS script.
This configuration caused multiple conflicts in source allocation, loaded drivers, and active services, causing legitimate antivirus services to crash and become unusable.
Next, the hackers installed Mimikatz for harvesting login credentials and FRP for remote access and created scheduled tasks to gain persistence.
In addition, Windows Defender was disabled to make detection impossible, event logs were manipulated, and system logging on the compromised systems was modified.
Other malicious actions included using tools like everything.exe, Certify.exe, and kerbrute for network exploration, generating ADFS certificates, and brute-force attacks on AD tickets.
No ransomware attack
Third-party backups were flagged for destruction, but according to security researchers, the hackers did not succeed. Also, no data encryption was observed, ruling out a possible ransomware attack. Therefore, the type of attack that was attempted via the vulnerability in Microsoft SharePoint remains unknown.
Microsoft already released a patch for CVE-2024-38094 in July. Therefore, users of Microsoft SharePoint are strongly advised to update as soon as possible.
Tip: Microsoft leads SharePoint workflow users to Power Automate