Hackers are attempting to spread the malicious software framework Winos4.0 to Windows endpoints via game-related applications to gain complete control. The now-discovered malware is a rebuilt variant of Gh0strat and bears similarities to CobaltStrike and Silver Fox campaigns.
Gaming-related applications, for example installation tools or optimization supplies are infected for spreading the Winos4.0 malware to Windows-based machines, FortiLabs security specialists discovered.
The malware found in gaming-related applications appears to be constructed based on the Gh0strat trojan and contains several components that handle different tasks.
The malware’s goal is to gain full control over infected Windows systems. For this purpose, the malware collects information about the infected hosts, such as IP addresses, the OS used, information about the processor, storage medium, network card, directory name and times.
The malware also checks whether system monitoring and anti-virus software is running on the affected machine. It also looks for a crypto wallet extension, saves the information found, takes screenshots, steals documents and monitors users’ activities.
Last, but not least, a module in the final attack phase causes a persistent backdoor to the hackers’ C2 server to be set up to maintain a long-term presence on the affected machine.
Attack in four phases
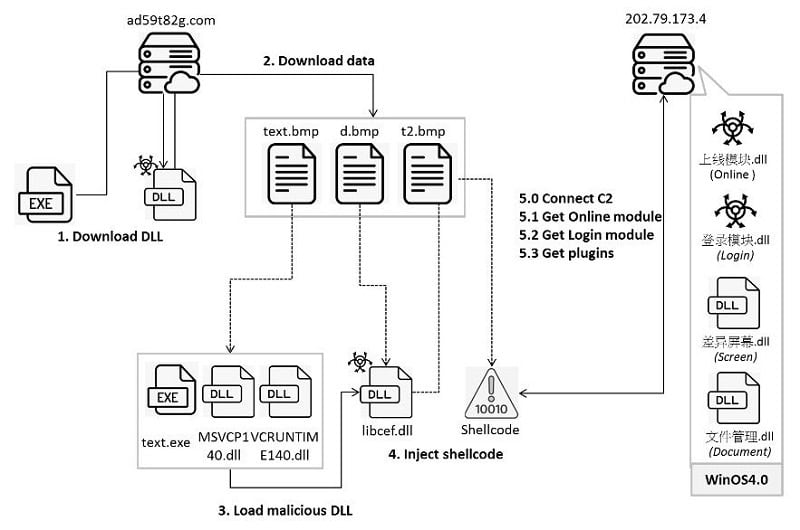
The attack path proceeds in four phases. In the first phase, victims are tricked into downloading a gaming tool. Upon running this application, a fake BMP file creates a DLL file that sets up the malware’s running environment, injects shellcode and achieves persistence. This Chinese-looking DLL file, “学籍系统,” would possibly target mainly educational organizations.
In the second stage, the injected shellcode loads malicious APIs, retrieves the command-and-control (C2) address and sets up traffic with this server. As the third stage in the infection process, the DLL file “上线模块” downloads encrypted data from the C2 server and stores it in a registry.
The fourth and final step of the process deploys the DLL file “登录模块” with the main malicious payload. This payload eventually executes all malware actions on the affected machine.
CobaltStrike and Silver Fox
According to FortiLabs experts, the Winos4.0 attack now being carried out bears some striking similarities to attacks carried out via the CobaltStrike tool and Silver Fox trojan.
Although the Gh0start trojan has now been (re)used for this purpose, the reuse or retooling of components closely resembles modifying the aforementioned software and malware to allow malicious actions to occur. For example, Winos4.0 was used in the Silver Fox campaigns, perhaps by Chinese state hackers.
Also read: ‘Pygmy Goat’ malware helps Chinese state hackers attack networks