Security researchers have discovered a new botnet called GoldBrute. The botnet attacks Windows systems that have a Remote Desktop Protocol (RDP) connection to the Internet.
According to researcher Renato Marinho of Morphus Labs, 1,596,571 RDP endpoints have been attacked. This number will most likely increase in the coming days, according to ZDnet.
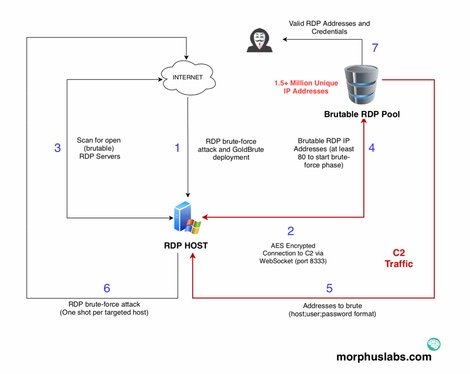
The botnet forces access to a Windows system via RDP. It then downloads a ZIP file containing the GoldBrute-malware code. GoldBrute then scans the Internet for new RDP endpoints, which are not yet part of the GoldBrute list of RDP endpoints. After the botnet has found 80 new RDP endpoints, the list of IP addresses is sent to the external command and control server. The infected host receives a list of IP addresses to carry out a gross force attack. For each IP address there is only one username and password, which the bot must try to verify. Each GoldBrute-bot gets a different combination of username and password. The bot attacks and reports the result back to the C&C server.
Increase in infected devices
For now it is not yet known how big the GoldBrute-botnet really is. However, it is clear that the botnet’s list of gross RDP targets has grown in size in recent days, as it steadily found new RDP endpoints to counter attacks. This growth in targets suggests that the number of infected devices has also increased.
Every system infected with GoldBrute only starts one password gambling attempt per victim. This prevents the intrusion of security systems that provide protection against brute-forcing. This is not good news for companies and users with RDP endpoints that are shown on the Internet, as it makes this botnet difficult to detect and stop. It can be said that gross force attacks currently pose the greatest threat to RDP systems that are exposed online.
BlueKeep
The GoldBrute botnet activity indicates that miscreants still use classic gross forcing techniques instead of using BlueKeep to target RDP endpoints, says Troy Mursch, founder of Bad Packets.
According to security company statistics, RDP scans for BlueKeep vulnerability account for only 3.4 percent of all RDP traffic in the past week. RDP attacks with brute force and attempts to exploit older RDP vulnerabilities account for the remaining 96.6 percent. . .
The fact that hackers do not seem to have found a way to abuse the BlueKeep vulnerability for the time being does not mean that companies can postpone patches. Microsoft and the NSA therefore call on users to implement security updates as quickly as possible.
Related: Million pcs vulnerable to dangerous Windows leakage
This news article was automatically translated from Dutch to give Techzine.eu a head start. All news articles after September 1, 2019 are written in native English and NOT translated. All our background stories are written in native English as well. For more information read our launch article.