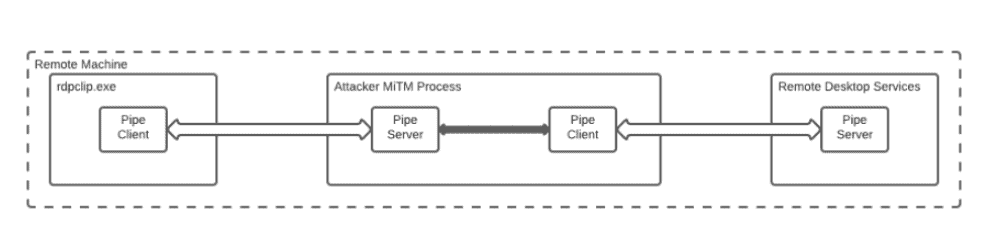
A vulnerability in the Windows Remote Desktop Protocol (RDP) allows users connected to a remote machine to access connected devices of other users. The threat was recently observed by security specialists at CyberArk Labs. Hackers can exploit the vulnerability for a Man-In-The-Middle (MITM) attack.
The Windows RDP protocol vulnerability was classified as CVE-2022-21893. Every user of a machine connected by RDP is also connected to the devices of other users connected via the same protocol. Users can gain remote access to devices of other users.
According to CyberArk Labs, hackers can exploit the vulnerability to easily carry out man-in-the-middle attacks. They can gain access to other users’ clipboard data, disks and folders. Authentication can be spoofed through smartcards.
Tool for compromising communication channels
The researchers succeeded in developing a tool to compromise the virtual channels of the Windows RDP protocol for communication between (company) servers and machine clients. If hackers succeed in intercepting the authentication and verification of the smart cards and associated PINs, the leak can escalate. Hackers would gain authorization to change access rights, allowing them to penetrate deeper into a corporate network.
Important to solve
CyberArk Labs qualifies the Windows RDP vulnerability as severe. Employees working from home often access their company environments through the protocol. Because remote work has become the norm, the vulnerability’s attack surface is large.
Microsoft has released a patch for all vulnerable Windows OS and Windows Server versions.