
Security

Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
Timeline

Log4Shell still a big problem after nearly a year and a half
According to Arctic Wolf research, the Log4Shell vulnerability is still being massively abused a year after i...
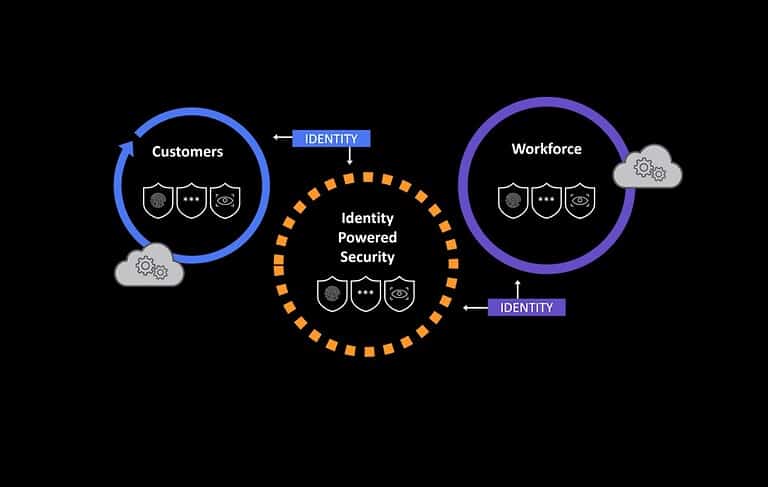
Zero trust in complex environments: how to ensure secure access to apps?
Many companies have seen their infrastructure and application landscape become more complex. This, in turn, c...

Splunk updates Security and Observability Cloud for better resilience
Splunk is releasing new functionality for its Security and Observability Cloud. This is to help companies bec...

Attackers target .NET developers with malicious NuGet packages
Developers are being attacked by threat actors using "sophisticated typosquatting techniques". Threat acto...

Ferrari has disclosed a data breach
The breach compromised some of Ferrari's IT systems, after which the company received a ransom demand from ha...

Only 8 percent of Dutch companies prepared for cyber threats
Only 8 percent of organizations in the Netherlands are prepared for modern cyber security threats, according ...

Emotet malware now distributed by Microsoft OneNote email attachments
The move intends to bypass Microsoft security restrictions and infect more targets. Emotet is a notorious mal...

Zscaler provides Posture Control with DLP and threat intelligence
Zscaler has added new functionality to Posture Control for securing applications. Data loss prevention (DLP) ...
NordPass announces passkeys solution to tackle the password problem
NordPass, part of NordVPN, is announcing the development of its new password storage solution: NordPass Passk...

Orange Cyberdefense and Microsoft collaborate on managed security services
The Managed Workspace Protection and Managed Threat Detection services are designed to help businesses across...