
ISO 27001 inspires confidence, but it is only the beginning
ISO 27001 certification is anything but easy. Nevertheless, security standards create a false sense of securi...

ISO 27001 certification is anything but easy. Nevertheless, security standards create a false sense of securi...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.

Chinese state hackers infiltrated the systems of cybersecurity company F5 at the end of 2023 and remained und...

A scan has revealed that more than 266,000 F5 BIG-IP instances are accessible from the internet due to the se...

A new attack campaign, dubbed Operation Zero Disco by Trend Micro , exploits a vulnerability in Cisco's Simpl...

North Korean threat actor UNC5342 is using a new technique to spread malware via public blockchains: EtherHid...

Critical infrastructure organizations are facing a new wave of cyber risks. Although the number of data breac...

F5 has released security updates following a large-scale cyberattack believed to have been carried out by Chi...

Hackers from an unknown country infiltrated F5 Networks' IT environment for months. Access to the development...
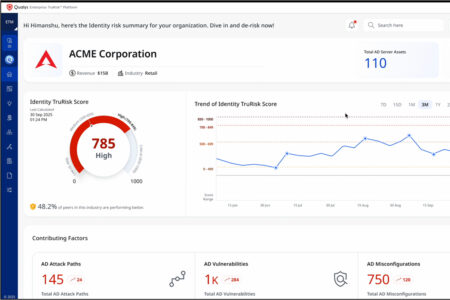
Qualys is expanding its Enterprise TruRisk Management (ETM) platform with three new AI-driven capabilities de...

NTT DATA and Fortanix announce a global partnership to help companies transition to post-quantum cryptography...

Security researchers are warning of a large-scale campaign. Attackers compromised more than 100 SonicWall SSL...