
Why did so many security vendors abandon MITRE’s stresstest?
This year, MITRE made headlines primarily because its leading vulnerability database was in danger of being d...

This year, MITRE made headlines primarily because its leading vulnerability database was in danger of being d...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.

At SoftwareONE they try to select the best solutions in the security landscape. Let's face it, the number of ...

Google Cloud's acquisition of Mandiant has been completed. The security and software company will continue to...

Researchers from security firm Binarly warned of unpatched vulnerabilities in HP firmware. Some of the vulner...

JumpCloud launched a password manager for IT administrators and managed service providers. JumpCloud devel...

Lampion malware has been spreading in higher numbers as of late. Threat actors exploit WeTransfer as part of ...

GIFShell is attacking Microsoft Teams users by making them download malicious files on their system via GIFs....
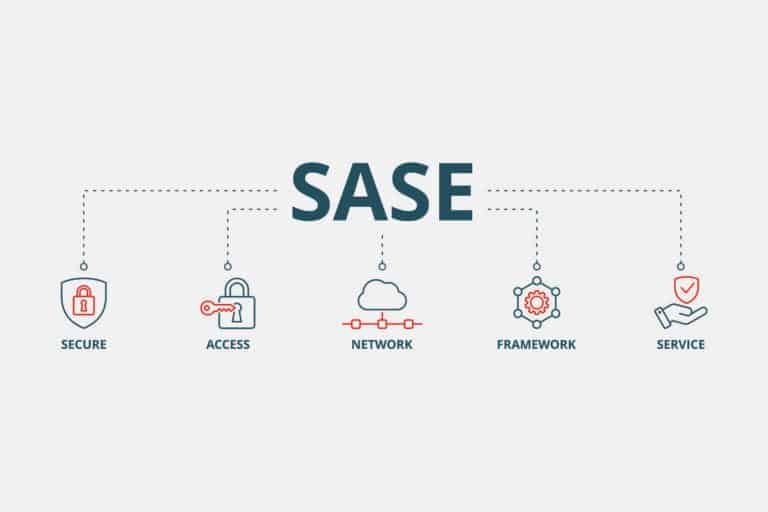
GTT is fully committed to SASE, or Secure Access Service Edge. It does so in its own way. We spoke with Mark ...

Artificial Intelligence (AI) is becoming more dominant in the cyber space. It can ensure that systems and bus...

The Portuguese Armed Forces General Staff Agency (EMGFA) reportedly fell victim to a hack that resulted in th...

A recent report by Trend Micro suggests that SMBs are the weak link in IT supply chains. Ransomware is on...