
Wiz sees big impact of AI on runtime security, but also stresses old threats
Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...

Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
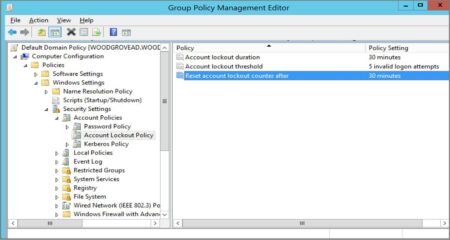
Upcoming Windows 11 versions will block accounts after ten failed login attempts. The setting has been availa...

Neopets confirmed that one or more attackers recently broke into the company's database. According to an anon...

Atlassian warns users of vulnerabilities in nearly every product, including Bamboo, Bitbucket, Confluence, Fi...
Salt Security launched a new version of its API Protection Platform. Users now have insight into the attack m...

The Belgian government accuses Chinese cybercriminals of carrying out sophisticated APT attacks on Belgian go...
Stytch introduced a new password-based authentication solution. According to the company, a whopping 85 perce...

Juniper Networks patched a large number of critical vulnerabilities in various networking and controller solu...

An exploit in macOS could allow hackers to bypass sandbox securities and execute code. Microsoft urges users ...

Security provider CyberArk unveiled a new security solution for AWS and several improvements to its current p...

A new survey on edge computing says remote working is leading to increased vulnerability. A survey release...