
Wiz sees big impact of AI on runtime security, but also stresses old threats
Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...

Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.

Hackers in most cases will return to take a second bite at the apple. The COVID-19 pandemic has led to a w...

The ALPACA attack profile uses domain confusion to fool secure web servers. Researchers in Germany have id...

The European Commission has started taking legal action over violations in privacy laws against Belgium. They...

Cyber criminals took advantage of the pandemic to increase their activity CNN this week reported that sign...

Cisco’s Webex Suite introduces some exciting updates after the acquisition of Slido s.r.o and Socio Labs In...

Palo Alto Networks introduced five new capabilities to the cloud security posture management of Prisma Cloud....
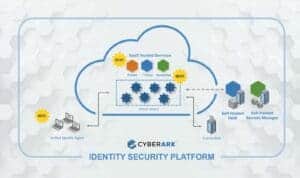
During CyberArk Impact Live, CyberArk announced new enhancements to its Identity Security Platform. With this...

The new vSIRIS software aims to provide deployment flexibility to help business continuity and disaster recov...

GitHub, the open-source platform for developers, has officially stated that they are updating their site's po...
Palo Alto Networks revealed that it discovered the first known malware targeting Windows containers. It ha...