Basically, you use a Synology NAS to store data, but you need to do so in a secure way. That’s where data protection features can help. In this article, we explain how secure a Synology server is.
Synology is one of the biggest players in the NAS device market. It gained that position by focusing heavily on storage in the past. Yet this area of focus alone is no longer enough. Increasingly, the importance of data security is growing. After all, data is increasingly sensitive and crucial, so hackers are also targeting it. Synology is aware of this and it is safe to say that security has currently become one of the company’s absolute priorities.
Full data protection
Synology does have an idea about how businesses can securely set up their NAS servers. In doing so, it talks about full data protection. That includes making the functionalities available for a tiered backup plan to achieve the highest possible availability for data and services. If your business is hit by an incident – that could be downtime due to power loss, but also unreachable data due to ransomware, for example – you want to minimize downtime. As far as Synology is concerned, that’s why you combine multiple solutions. The image below gives an idea of what that would look like.
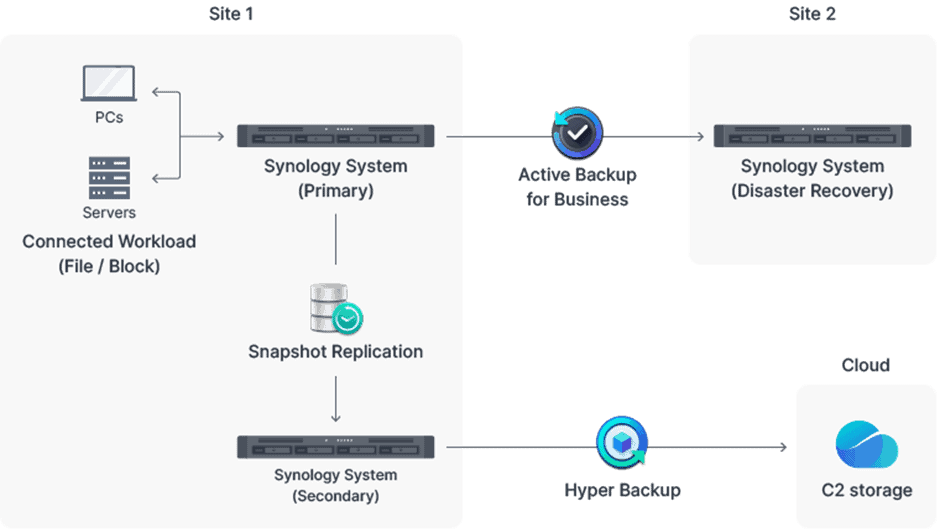
First, in this ideal scenario, on-site protection is achieved. The data from PCs and server are stored on a Synology NAS, the primary location. The data from the primary device is also placed on a secondary system with Snapshot Replication. Snapshot Replication creates copies of shared folders and LUNs for replication to the other NAS. For example, for shared folders, snapshot and replication times of five minutes can be set, compared to every 15 minutes for LUNs. Then, in the event of data loss or accidental modification of data, data must be quickly recoverable. The original NAS should then have the original data again within seconds.
Completing steps
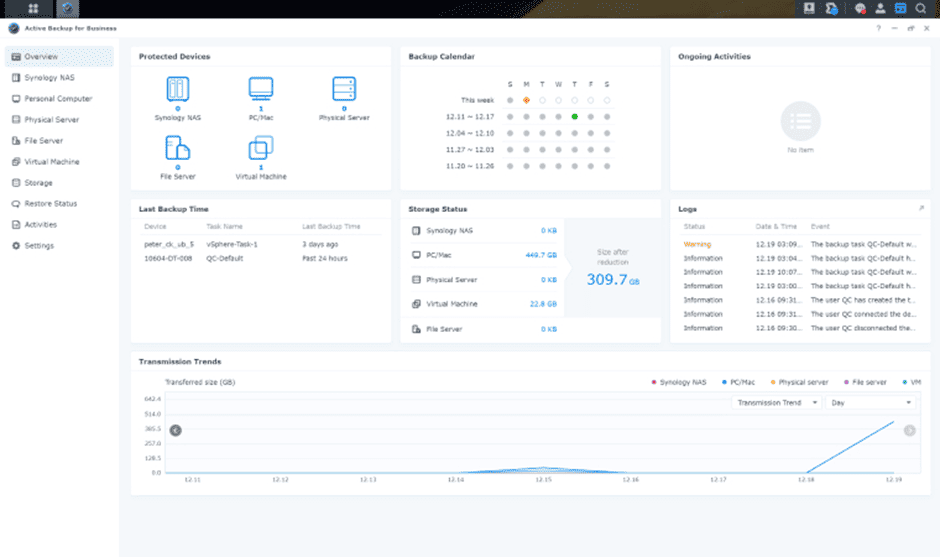
With this, you have taken the first step toward a solid data protection plan. Next, ideally, you will look at what you can do to store data in other locations as well. For the primary storage system, that data can be stored at a remote Synology device. To such a location you can copy settings and packages in addition to the data from the primary storage location. For this purpose, Synology has Active Backup for Business, a dashboard for setting up and monitoring backup tasks. The AES-256 encryption standard can be used to better protect backups from data breaches. If things do go wrong, data can be restored through a recovery portal.
The final part of a successful cyber protection strategy is realized, as far as Synology is concerned, by backing up the secondary system. In this case, the cloud serves as the basis for those backups. Synology offers within Hyper Backup the ability to set up a backup plan, for example to set up a backup schedule or schedule checks for corrupted data. Again, encryption standards can be set. Synology then gives users the choice of which cloud environment to back up to. You can bring the data to a cloud service like Google Drive or Dropbox, as well as any S3-compatible storage provider. In addition, C2 Storage gives you the option to use a cloud location from Synology. The NAS brand sees this as an absolutely secure place for your data in the cloud.
Active Insight
The above strategy combined with the supporting features bring maturity to your company’s NAS landscape, ensuring data is properly secured. Yet as you expand your infrastructure, a new issue may arise; how do you ensure that NAS server performance and statuses are maintained? That’s where Active Insights within operating system DiskStation Manager is available for. With this software, it is possible to monitor and protect all your NAS devices.
Also read: Synology RT6600ax router review: ideal router for small business environments
For example, Active Insight analyzes static data from your servers to display performance and health status. The health status in this case means the memory consumption of each NAS, as well as the performance and load averages of CPUs. The portal also provides live and historical insights into data usage, IOPS performance and more, so administrators can better determine where resources are needed. Finally, it shows how the network is performing, allowing Active Insight users to examine device throughput and latency.
A secure NAS infrastructure
There is functionality within Active Insight to take data and access protection to the next level. Indeed, because of the centralized nature of Active Insight, the software lends itself well to monitoring Hyper Backup job statuses and reviewing backup logs. It should prevent unexpectedly important issues or tasks from being missed within your data protection strategy anyway.
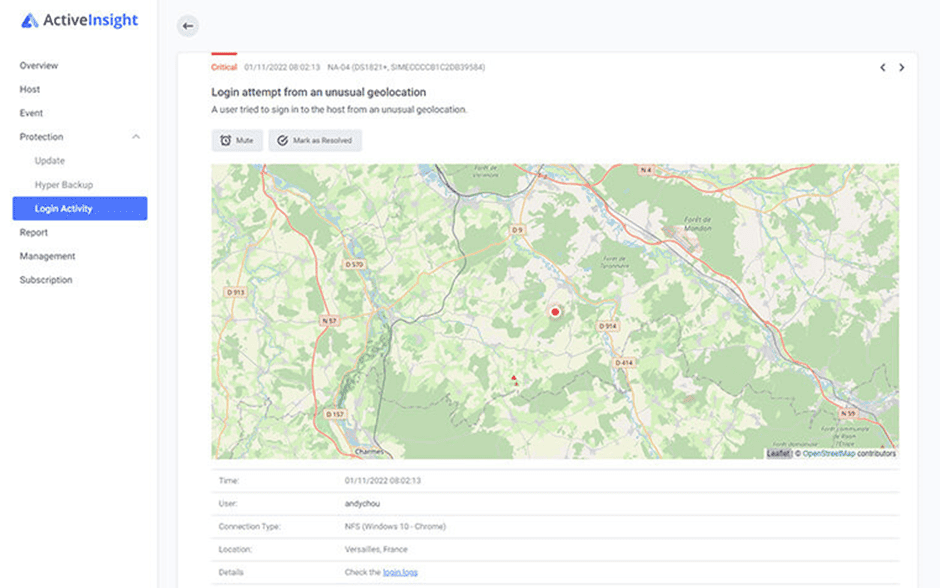
The image above shows a specific feature of the monitoring platform. You can see the ability to view detailed information about login activity. In fact, Active Insight can detect an abnormal pattern and send a signal about it. An example of an abnormal pattern is a login attempt by a user from an unusual location. It may be reason to do some further investigation to rule out malicious activity.
Another useful thing for administrators of a NAS infrastructure is the ability to control updates through Active Insight. The platform provides insight into the update status of Synology devices. If the NAS devices do not yet have the desired updates, the installation can be initiated via Active Insight. However, the functionality as we describe here requires a proactive attitude on the part of the administrator. Synology manages the risk of missing out on new updates by sending notifications that a new update is available.
Tip: NAS servers make backups affordable through on-premises and cloud
The first priority
All in all, Synology offers quite a few features for securing data on NAS devices, and there is also plenty available for securing the servers themselves. The brand now claims that security is its first priority. This is prompted by the fact that “businesses face a challenge to offer secure access for a broader array of services and applications while guarding against increasingly sophisticated threats.” In addition, Synology’s security features aim to provide businesses with the tools to “quickly to evolving technologies, business needs, and threats.”
In itself nice words, but what actually shows that Synology is pursuing this is the provision of the PSIRT. The Product Security Incident Response Team is a great way for tech vendors to demonstrate their commitment to a high level of security. The PSIRT ensures that the proper response comes to a security incident on a NAS. For example, suppose a zeroday is found, Synology aims to complete the vulnerability assessment within eight hours. Then Synology produces a fix for the vulnerability within 15 hours. That would mean a zeroday found would be fixed within 24 hours.
Part of the PSIRT is the bounty program, which invites hackers and security researchers to contribute to the security of NAS servers. Rewards from the bounty program run as high as $20,000 (about €18,200), which can encourage ethical hackers to look for vulnerabilities and report them to Synology.
With that, the path to a secure NAS landscape is something Synology offers the necessary support in. The NAS vendor has features available to let you as a business manage data security, but also tries to ensure secure systems yourself with the necessary basic steps. All with security as the first priority.