
Insight:
Security Platforms

Separate security measures are often limited to a single function or threat type—think antivirus software, firewalls, or encryption. With an integrated security platform, these can be managed and coordinated from a single environment.

Cybersecurity needs AI as much as AI needs cybersecurity
AI is not new, not even in cybersecurity

There is no OT apocalypse, but OT security deserves more attention
Real ransomware attacks on OT are rare

AI, quantum threats, and the evolution of securing the endpoint at HP (Ian Pratt, HP)
This week's episode of Techzine Talks on Tour was recorded several months ago. At the HP Amplify Partner Conf...

CyberArk extends PAM solution to machine identities
Like a spider builds a web, CyberArk is continually increasing the number of profiles for which it has securi...
Timeline


Thales covers data security entirety thanks to Imperva
A year and a half after Thales acquired data and application security company Imperva, the two technologies h...
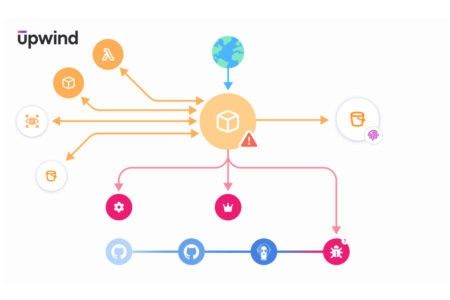
Upwind adds API security capabilities to cloud security platform
Upwind adds real-time API security to the Cloud Application Detection and Response (CADR) framework. This sho...
Cisco AI Defense enables secure deployment of AI
Further expansion for Cisco's security platform

Arctic Wolf CEO: “Platform is what customers are really looking for”
The security platform is gaining traction

ReliaQuest brings autonomous cybersecurity step closer with AI Agent
More than 15 years of ReliaQuest's experience comes together in AI Agent, which handles everyday Tier 1 and T...

Microsoft cleans up its cloud systems
Company removes hundreds of thousands of unused apps and millions of inactive tenants


Huge database of sensitive info exposed to the internet
Some 31.5 million invoices, purchase orders, contracts, patient forms, and other sensitive documents have bee...

From encryption to exfiltration: how do you secure and protect your data?
Major investments in IT security don't seem to deliver results

Companies are finally prioritizing OT security, and they need to
Cisco research shows a promising trend. OT security has long been neglected, but organizations are finally ca...

Rubrik and Mandiant join hands to secure backups
Security company Rubrik is integrating threat detection technology from Mandiant into its backup solutions. T...

CrowdStrike licks its wounds after catastrophic update
The aftermath of Friday's global disruption caused by a CrowdStrike Falcon sensor is becoming clearer. On Sat...

Global IT outage due to botched CrowdStrike update: what went wrong?
IT incident with massive impact should never have happened

List of Snowflake customers affected since Ticketmaster leak continues to grow
The list of companies whose data has been captured in the massive data theft from Snowflake environments keep...

NinjaOne MDM brings Android and iOS together on one console
Supporting hybrid working on one central platform

Fraud with deepfakes: how can an organization protect itself?
Deepfakes require employees to develop a different attitude to digital multimedia. Since we have deepfakes, e...

Old encryption technique in RADIUS protocol opens doors for hackers
Authentication protocol used extensively in corporate networks

Companies increasingly ‘re-victimized’ by cybercriminals
Cybercriminals are increasingly trying to extort companies multiple times when their data has been captured. ...

European consumers worry about online security and AI influence
Europeans are quite concerned about digital identity theft and the potentially detrimental role of AI in onli...

Half of businesses experience VPN-related attack
Figures from Zscaler show that in the past year, 56 per cent of organizations were targeted by attacks that e...

“Firewalls will become like mainframes, Zero Trust is the way forward”
Zscaler CEO Chaudhry sees that Zero Trust cannot be ignored.

KnowBe4 and Microsoft introduce new anti-phishing feature for Outlook
KnowBe4 and Microsoft have joined forces to improve email security in Outlook by introducing the Microsoft Ri...

LockBit’s claim of large-scale attack on Federal Reserve turns out to be false
Update, 28/06, Laura Herijgers—The doubts about the ransomware attack on the Federal Reserve have proven to...

Ransomware attacks are increasingly used as cover for espionage activities
Cyber-espionage groups are increasingly using ransomware attacks to make their attempts at sabotage and data ...

Makers of infamous xz backdoor cleverly managed to cover their tracks, analysis shows
The backdoor in the xz compression tool for Linux that came to light earlier this year used several sophistic...

Security systems struggle with malicious QR codes made from ASCII characters
The number of phishing attempts using QR codes (quishing) is on the rise, according to Check Point Research. ...

Up to 5 million dollars demanded from Snowflake customers for return of captured data
The cybercriminals who recently broke into Snowflake customers demand between 300,000 and 5 million dollars (...

Vulnerabilities in VMware’s vCenter Server enable remote code execution
VMware by Broadcom has disclosed two critical vulnerabilities in vCenter Server, a key component for managing...

Cybersecurity label should not exclude AWS and Azure warns European industry
26 European industry groups warn that the European cybersecurity label for cloud services should not exclude ...

An inside-out look at cyber security from Arctic Wolf CISO Adam Marrè
In this new episode of Techzine Talks on Tour, we take an inside-out look at cyber security. That is, we disc...


Ticketmaster incident shows: attackers no longer break in, but log in
Ticketmaster, Santander, and Advance Auto Parts are believed to have been robbed of customer data by the same...

The tables are turning in favor of the defenders in cybersecurity (Jeetu Patel, Cisco)
For this new episode of Techzine Talks on Tour we sat down with Jeetu Patel, EVP of Collaboration and Securit...

International ‘Operation Endgame’ deals sensitive blow to cyber criminals
A major international police operation called 'Operation Endgame' has disrupted a massive system of botnets. ...

What is ‘credential stuffing’ and how do you defend against it?
Okta and Cisco recently warned of an unprecedented spike in "credential stuffing" attacks. What does that ent...

xz backdoor shows how vulnerable open-source is to hackers playing the long game
A security leak in the Linux compression tool xz shows open-source systems' vulnerability to multi-year infil...

Can the right cybersecurity solution make Verstappen’s Red Bull go faster?
Formula 1 is all about speed. A team's cybersecurity solution must keep up with this. We spoke to Mark Hazelt...

CrowdStrike: Navigating the sprawl of endemic automation
Cyber security and application security endpoint posture management company CrowdStrike has explained its mis...

API security is starting to get the attention it deserves from organizations
Recent research by Noname Security shows that many organizations say they understand that they need to proper...