Chinese researchers have cracked the fingerprint security of Android phones through a brute-force attack: BrutePrint. This allowed them to take control of the devices.
According to the researchers from Tencent Labs and Zhejiang University, the BrutePrint attack allows hackers to bypass the user authentication of Android phones and take over the device.
Three vulnerabilities
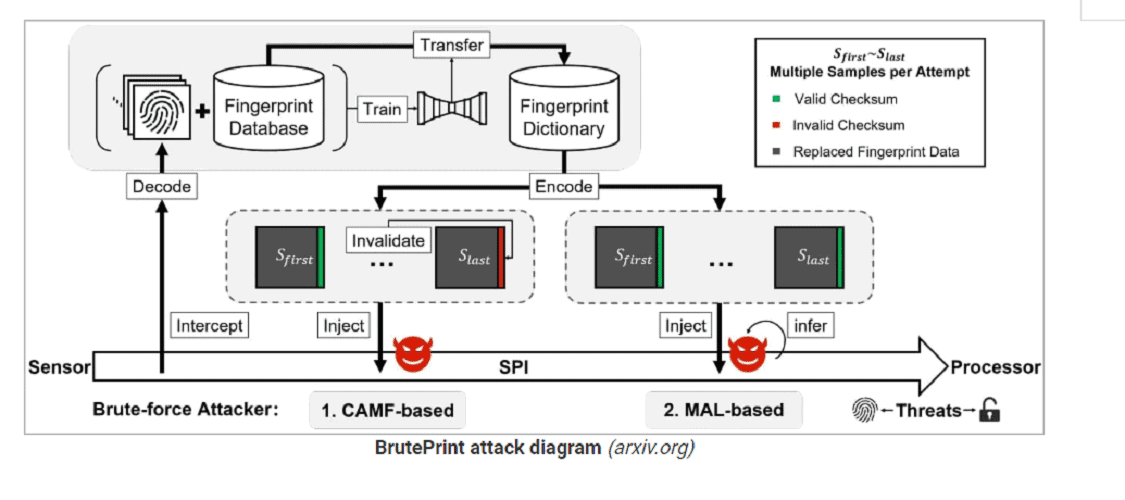
They discovered that two zero-day vulnerabilities, Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL), can bypass existing security measures on Android phones. The biometric data on the fingerprint sensors’ Serial Peripheral Interface (SPI) is also poorly secured. This ultimately enables a man-in-the-middle (MITM) attack to hijack fingerprint images.
BrutePrint Attack Features.
In a BrutePrint attack, an unlimited number of fingerprint images are sent to a device until there is a match. To perform the attack, hackers need access to the affected device and a database of fingerprints available through academic datasets or biometric data leaks. The required hardware costs just $15.
The CAMF vulnerability injects a “checksum error” into the fingerprint data to stop the authentication process at an earlier time. This allows hackers to “try” unlimited fingerprints, while security systems do not record failed attempts.
The MAL vulnerability helps infer authentication results from fingerprint images that hackers try out. This also works in ‘lockout’ mode, i.e. after multiple incorrect login attempts.
The final component is a ‘neural style transfer’ system. This should convert all fingerprint images in the database into prints scanned by sensors. This makes these images valid and more likely to give a successful breach.
Also read: 9 million Android devices contain pre-installed malware