Research by cybersecurity firm Trustwave indicates that Microsoft’s popular MSSQL service is getting attacked at an alarming rate.
SQL services contain relational databases, which are pivotal for all kinds of applications that access data from them. They are also popular targets for cybercriminals because they may contain sensitive data, from intellectual property to customer information. Oracle, MySQL and Microsoft SQL are the most commonly used database management services in this market.
Honeypots
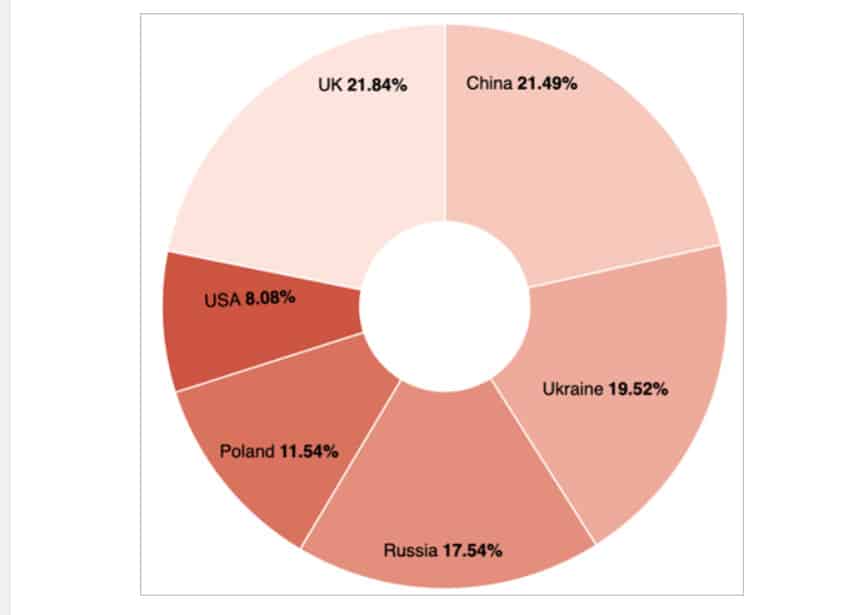
The Trustwave study covered a limited number of countries. It chose to monitor the U.S., UK, Poland, Ukraine, Russia and China. The rationale behind this selection was that these are geopolitically tense states, with a rich array of malicious actors who would be on the prowl for sensitive data to disturb businesses and harm adversarial states.
Specifically, Trustwave employed so-called “low-interaction honeypots.” That means they were decoy targets hosted on SQL services that had no other system set up for attackers to get into. They were purely intended as sensors to see if an attack was taking place, but not how these criminals were operating.
As far as the United Kingdom and China go: these countries are sort of data hubs, with a lot of information they house for other countries. Perhaps that explains why these two countries could count on the most MSSQL attacks. As for Ukraine and Russia, few can have any doubts as to why they would be attacking each other virtually.
MSSQL by far the most attacked
One quickly noticed a trend: the Microsoft SQL service was suspiciously targeted. Within the testing period (4 months from Dec. 6, 2022), more than 50 million login attempts took place on that service, which amounted to 93 percent of all attacks. So striking that Trustwave is still conducting further research, due later this month.
Trustwave characterizes the attacks on MSSQL as “very intense”. Also, the distribution of attacks was very different from MySQL and Redis. In these two cases, UK constituted the majority of measured login attempts (54.72 percent for MySQL and 59.97 percent for Redis).
Protecting databases
Rather unsurprising is the advice Trustwave gives for a moment: namely, that it is important to properly protect databases. The well-known advice to maintain unique passwords and MFA, for example, is also included.
However, it is crucial to keep up with database security when it comes to vulnerability scanners. Trustwave cites its own AppDetectivePro, something to be expected, of course, but not unwarranted.
It is particularly striking how different the picture is per database vendor. For example, Oracle and IBM saw far fewer access attempts into Trustwave’s honeypots. They suggest here that it could be explained by the type of data stored there or that attackers are less aware of any vulnerabilities. Either way, we are very curious as to what is so special about MSSQL, so to be continued.
Also read: Database evolutions: caching in with schema-as-code
