Upcoming Windows 11 versions will block accounts after ten failed login attempts. The setting has been available for some time, but will soon be enabled by default to prevent brute-force attacks.
The setting blocks Windows accounts after ten failed login attempts. A user can try again after ten minutes. As a result, it’s much tougher to carry out brute-force attacks.
Brute-force attacks
Brute-force attacks are common. Hacker use software tools to attempt a huge number of passwords in a short space of time. The longer the tool runs, the higher the probability of a match. Hackers need a way to input passwords.
As such, brute-force attacks are impossible without PC access. The Remote Desktop Protocol (RDP) of Windows makes it possible to gain remote access. RDP only works for those that have a PC’s network address and a user’s account details. This data can be lost in several ways.
Microsoft could prevent brute-force attacks by tightening RDP security, but that would ruin its ease of use. Resultingly, the tech giant is implementing another solution.
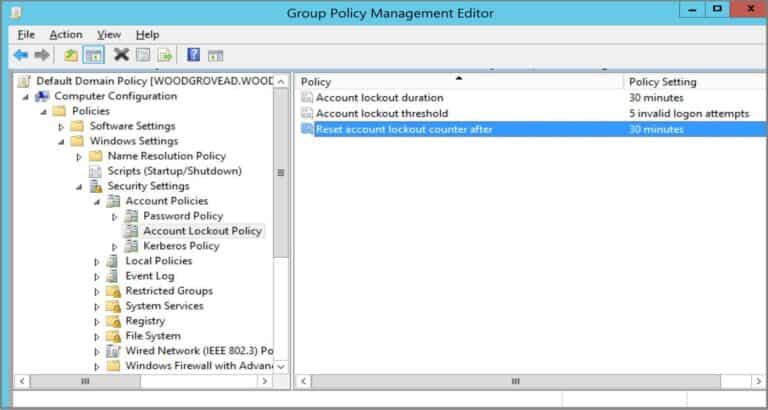
Account lockout policy
The ‘account lockout policy’ has been available in the policy settings of PCs and admin tools since Windows 10. The function was always disabled by default. That’s about to change.
“Win11 builds now have a DEFAULT account lockout policy to mitigate RDP and other brute force password vectors”, Microsoft Enterprise and OS Security VP David Weston wrote on Twitter. “This technique is very commonly used in Human Operated Ransomware and other attacks — this control will make brute forcing much harder, which is awesome.”