
Security

Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
Timeline

Android malware bypasses biometric scan and steals phone PIN
The so-called Chameleon malware is not new, but it has worrying new capabilities. Android users can download ...
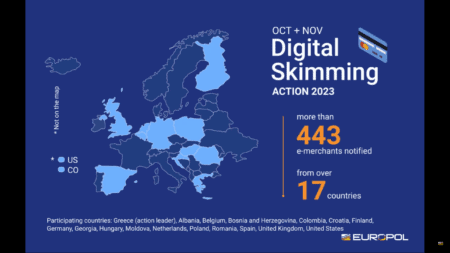
Digital skimming: credit card info stolen from 443 online stores in 17 countries
Europol announces that credit card data from 443 online stores from 17 countries has been stolen. Seventeen c...

Google Chrome has Safety Check: controls and needs control
Google is working on the security of the Chrome browser for the desktop. The functionality of the feature is ...

Explosive rise in ransomware attacks since 2022
The number of ransomware attacks continues to increase worldwide. This is despite a previous dip in the numbe...

SentinelOne XDR platform and Security Datalake get Gen AI boost
Security Datalake is taking on an increasingly central role in SentinelOne's offerings. XDR and the new Purpl...

Ivanti fixes 14 critical vulnerabilities in Avalanche MDM solution
Ivanti recently patched as many as fourteen critical security vulnerabilities in its enterprise MDM solution ...

New phishing campaign steals Instagram backup codes
A new phishing method aims to sidestep the two-step verification of Instagram accounts. A misleading email me...
Online data transfer not always secure with SSH protocol despite encryption
A new type of attack is targeting the Secure Socket Shell (SSH). This network protocol is used for data trans...

Decades after its debut, SMTP still enables new phishing techniques
A new form of e-mail spoofing was revealed this week: "SMTP Smuggling." The vulnerability allows threat actor...
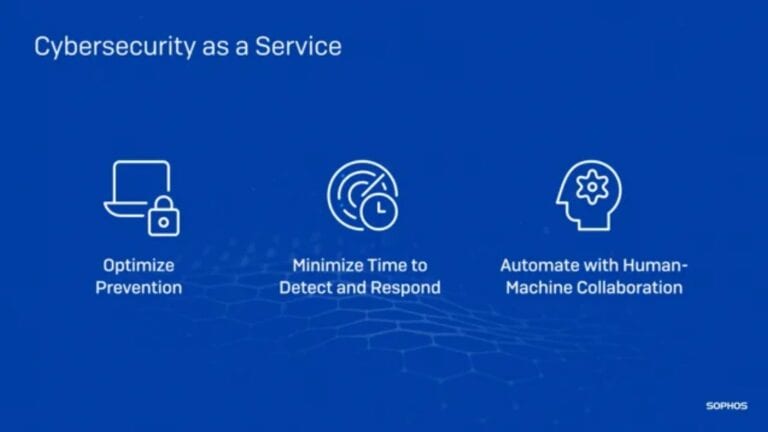
Sophos CSaaS is a shield against modern security threats
With cybersecurity-as-a-service (CSaaS), Sophos aims to protect companies from growing and evolving cyber thr...