Everything there is to find on tag: Check Point.

Check Point introduces Quantum Spark 1900 and 2000 firewalls for SMBs
Check Point's new next-generation firewalls are said to block 99.8 per cent of attacks. In the Quantum Spa...
Everything there is to find on tag: Check Point.

Check Point's new next-generation firewalls are said to block 99.8 per cent of attacks. In the Quantum Spa...

Users of Check Point solutions will soon be able to receive assistance from the Infinity AI Copilot. This sho...

Check Point is buying Security Service Edge (SSE) specialist Perimeter for around 446 million euros ($490 mil...

The number of global cyber attacks has risen to a new high in the past year. This is according to researchers...

Hackers increasingly target Python repositories. Security experts from Check Point recently discovered ten ma...

According to Check Point, ransomware strikes one out of 40 organizations per week. In its latest report, the ...

Check Point Software introduces Quantum Lightspeed, a series of new firewalls for data centers. The firewalls...

Adobe has announced a partnership with Bolt for creating one-click checkout solutions for people using the fi...

Cybersecurity is in a state of constant change. The attack surfaces on which cybercriminals capitalize are as...
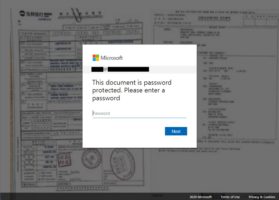
Log-in data of victims of phishing attacks were available on various hacked WordPress websites. These website...