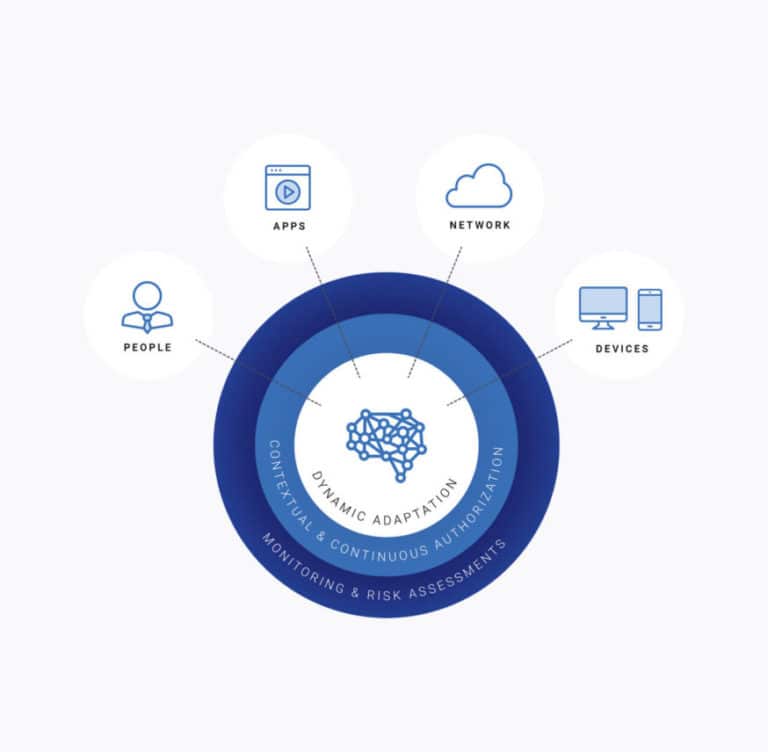
BlackBerry has been committed to securing company endpoints for years. The company particularly does this through Unified Endpoint Management (UEM) and Unified Endpoint Security (UES). Both security approaches aim to provide an answer to the growing number of devices within companies. After all, more devices also lead to new complexities in terms of security, management and visibility. During the recent BlackBerry Security Summit, the vision and direction were further discussed.
For years, companies have seen an increase in the number of endpoints connecting to their networks. These are usually devices running Windows, macOS, Android or iOS. But there are more devices accessing the network, such as Internet of Things devices. Therefore, it is expected that this growth will continue.
In addition to this considerable increase in the number of endpoints, devices are used everywhere. Laptops and smartphones are crucial for employees on the road or working from home. Ideally, only devices approved by the IT department should be used for this purpose, as security is then easier to guarantee. However, some employees prefer using their own devices, on which they have administrator rights. As a result, companies run into shadow IT, a risk that is expected to persist. After all, the current trend of working from home may very well continue for some time, and employees sometimes use their own laptops for their work.
Enterprises want as much control and visibility as possible, regardless of the endpoint type and whether or not they are managed. That way, they know what employees are using, and it is possible to push updates. BlackBerry can and wants to help with this.
Tip: BlackBerry secures mobile devices on the fly
UEM at the roots of management
The management and security of the devices can be simplified with Unified Endpoint Management. These platforms give companies a console to manage many different endpoint tasks. An administrator gets an overview of the used devices. In a simple case, you have a view of devices that have been rolled out by the IT department. For example, it becomes visible if a user deletes a certain tool, which is needed for the security policy. However, when a user does management by himself, UEM can still read data when the device connects to the enterprise network. This data shows which software is being used, so IT staff can give a signal if something is out of the ordinary.
UEM can ultimately be used for all kinds of actions. Imagine if your company decides to provide 1,000 employees with a new laptop, to better support mobile working. Then you’d want to equip these laptops with specific features. If the IT department has the admin rights to these laptops, they can easily perform such actions from the UEM platform, and there is little need to perform it manually. Besides, a UEM platform, for example, is also useful for rolling out policies from the IT department, so that endpoints neatly adhere to the compliance guidelines.
Artificial intelligence as additional security layer
UEM therefore really helps enterprises to secure and manage endpoints. However, it does not offer protection against everything. Complying with certain security policies requires too much manual work, but detecting cyber threats, for example, is not something UEM is fully tailored for. Additional security solutions are therefore needed. Solutions that have some overlap with UEM. If you unify these solutions and use them to complement each other, you reach a comprehensive cybersecurity approach.
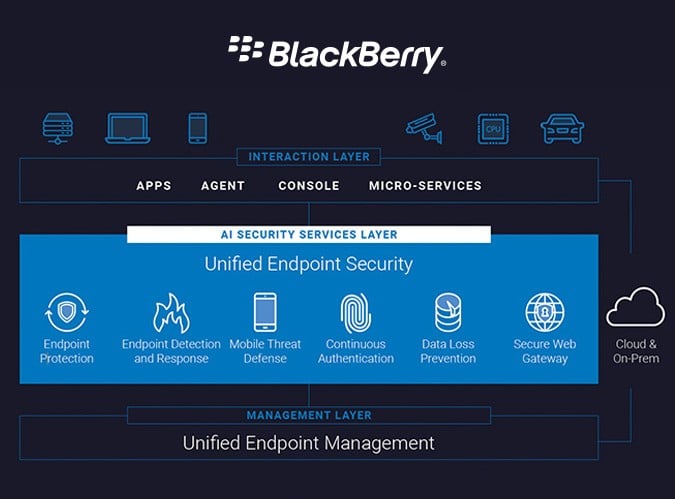
This approach, where all the tools collaborate and integrate as much as possible, is a response to the chaos in the security landscape. This chaos is caused by the growing number of cyber attacks, the growing complexity of attacks and the increasing number of company assets that need to be secured. It has become difficult for security professionals to navigate this complex landscape. That is why BlackBerry has developed an additional set of security services. This is a layer of security on top of UEM that protects companies from cyber threats and, if necessary, helps them recover from one. It includes the following services:
- Endpoint Protection – provides malware protection, protects the memory of entpoints and applies policy enforcement.
- Endpoint Detection and Response – uses artificial intelligence to, for example, prevent incidents, detect threats and provide comprehensive analysis of an incident.
- Mobile Thread Defense – prevents and detects advanced malicious threats at device and application levels.
- Continuous Authentication – uses BlackBerry Persona to assess whether a user can be trusted. This includes behavioural and process analysis.
BlackBerry also wants to add Data Loss Prevention and a Secure Web Gateway to this UES layer, in the future. These features should reduce the risk of data leaks and prevent unsecured traffic from gaining access to the company network.
Putting solutions together is the step forward
The solutions that BlackBerry has recently released or has planned, should integrate as much as possible. This would make it easier for companies to implement a security policy, as it is much more convenient to define policies directly across different security solutions. Having a uniform policy also means you get more visibility into the endpoint landscape of your business.
Additionally, the solutions can also fall back on BlackBerry’s artificial intelligence. Security professionals may lack some insight into incoming cyber threats, as the number of vulnerabilities and attacks can be very high. In that case, AI can be helpful by autonomously detecting cyber threats. AI can also be used to analyse an attack or validate user identities. The latter ensures that only the intended people are granted access to your system.
All in all, BlackBerry’s layered approach, in which UEM is the management solution and UES provides the additional security tools, makes sense. After all, many companies have a fragmented security approach because they use many different security solutions that all have their own qualities. Some of these solutions can easily be unified into one platform from a single IT vendor, making the work much easier. With that in mind, BlackBerry offers and unifies various tools to secure a large number of endpoints.
Tip: BlackBerry discovers hacker group selling their services