After multiple conversations about passkeys in recent months, I decided it was the right time to join the movement and explore whether a passwordless life could be mine… The alternative to passwords, known as passkeys, has been developed and promoted by the FIDO Alliance. The mission of the FIDO Alliance, an industry association, is to lessen the world’s dependence on passwords.
The primary benefits of passkeys are their resistance against phishing, the stronger security they offer, and the significant ease for those who still “remember” their passwords… And let’s be honest, it’s time for a change; aside from hackers, who actually enjoys dealing with passwords?
My key learnings from going passwordless:
- I felt like an early adopter since it is only implemented at a limited number of services. I will go “hybrid” with both passkeys and passwords.
- The implementation of passkeys varies per service. For instance at Apple, a device-bound passkey is used as second factor, while at Microsoft, it completely replaces the password. You can even remove the possibility to login with a password!
- In some implementations, you can fall back to “old” authentication methods like passwords or SMS, which cannot be turned off and weaken account security.
- In case a service does not support passkeys, a potential work around can be to use social login (with configured passkeys) if supported. This might come with a price in regards to your privacy.
- There is no strong incentive for companies to implement passkeys in their service. This might change with the implementation of NIS2; although “strong authentication” can also include SMS as a second factor. Furthermore, some companies like banks or gaming platforms have already implemented their own authentication mechanisms with their application on a mobile device.
Background on passkeys
The FIDO alliance defines passkeys as “a replacement for passwords that provide faster, easier, and more secure sign-ins to websites and apps across a user’s devices. Unlike passwords, passkeys are always strong and phishing-resistant“. This definition captured my attention, especially considering the endorsement of Apple, Microsoft and Google, who adopted the FIDO standard in their services between 2022 and 2023. Subsequently, numerous other services have implemented the passkey functionality since then. To find out which services support passkeys, check out passkeys.directory.
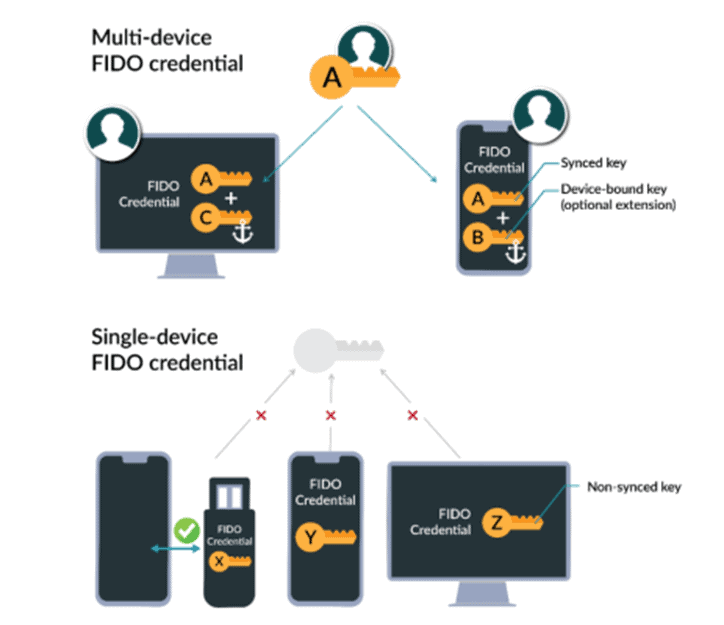
There are roughly two variations of passkeys, both with a certain level of convenience and security:
- Multi-device passkeys: this variation is focused on consumers, the passkeys are securely synchronized between the devices of the user offering a lot of convenience.
- Device-bound passkeys: this variation is regularly used by companies and individuals that require high security, the passkey remains on the device and cannot be copied. This is the least convenient variation because you always need to have access to the device with the passkey which improves the security…
The image below illustrates the difference between multi-device and device-bound passkeys. Passkeys can be stored on devices such as your phone or laptop, or on a dedicated hardware security key like the YubiKey or Googles Titan. In the case of hardware security keys the passkeys are device-bound.
Preparing to go down the rabbit hole
I decided to fully commit to high security and managed to get my hands on 3 YubiKeys for storing my device-bound passkeys. You might ask why three? Well, the “challenge” with device-bound passkeys is that they require the presence of the device for authentication. Additionally, it is also advised to have at least one back-up key because the passkeys typically replace the password. This means that the service will deny access when you try to login without the passkey in case you lose it. This also means that the set-up process is time-intensive because all three security keys need to be enrolled together…
My strategy was to leave one key at home, one joined my keychain and the last one found its place at work. Seems like a good approach, right? Furthermore, I secured the YubiKeys with a passphrase in case I might lose one so they cannot be used without it… This means that I always need a passphrase to unlock the security key and an “attacker” has 8 tries before all access is blocked to my passkeys.
Going down the rabbit hole
I decided to filter the top 10 most used accounts in my password manager and logged in to those platforms to check if they support passkeys. I began configuring passkeys in my accounts at Apple, Google, Microsoft and Amazon because they all implemented support for passkeys. I was about to find out that their implementation differs somewhat from each other:
Apple: The transition to passkeys at Apple was a bit scary because of all the warnings about potentially being locked out of your account if you lose your passkey. The YubiKey is used as a second factor at Apple after you provide the username and password, which defeats a bit of my goal but it offers strong security this way. Apple does allow passwordless login with their multi-device passkey which they heavily push. I did not find an easy way to sync this passkey from my mobile device to my YubiKey.
Google: For some reason I could not create passkeys using the Chrome or Edge browser but got it working with Firefox. In case you are enrolled in Google’s Advanced Protection Program they require a security key as a second factor, just as Apple’s implementation, because it’s a more secure way to sign in. The login process is quite easy after your provided your google account. However, you can still authenticate without a passkey if you have configured another second factor by using your account password and for example an OTP.
Microsoft: Microsoft seems to be the only party that literally let me remove my account password thus forcing the use of passkeys. Although, be aware that they heavily push their Microsoft authenticator. I like the Microsoft implementation the most. Especially because I do not even have to supply a username or email address when I want to login. I just click sign-in options -> security key and login with my passkey.
Amazon: Amazon was quite easy to configure although you can still login with a username and password.
After configuring these accounts, I looked into setting up the other services I regularly use. Unfortunately, not many services support passkeys yet, even after a few years of availability. I felt like an early adopter which I probably am, still after years of the availability? For instance, I would love to ditch the “master password” of my password manager and unlock it using my YubiKey. But it seems that the password manager I use, focused on securing their future first (phun intended) by implementing the support of passkeys in the password manager itself instead of the functionality required of unlocking the vault.
Furthermore, my bank and Steam, have both implemented their own authentication solution utilizing their mobile app. It seems that there is no incentive to implement FIDO2 for consumers for them. Also Netflix does not support it and Whatsapp only supports passkeys on Android at this moment. LinkedIn states that they support passkeys but that functionality is no where to be found in my account. Finally, there are the largest online retailers in the Netherlands, Bol and Coolblue, which do not support passkeys at the time of writing.

Conclusion
Unfortunately, I found the limited support for passkeys across services to be disappointing. I think greater adoption could be reached if there was a bigger incentive for companies to implement this technology.
One potential workaround for using passkeys on services lacking support could involve utilizing the Social login functionality, if available. This way you can login with a passkey with your social account on a third party service. A question you have to ask yourself is, if you want the third party to process and access information from your social account…
The potential of the technology is really good and it makes life easier and safer due to the resistance against phishing. However, I believe it will take several generations to phase out passwords, especially without a strong incentive to implement the technology. For now, I will adopt a hybrid approach to securing my accounts, using both passkeys and passwords. I will use passkeys on the services that support it, including my most valuable accounts, and will use randomly generate passwords and one time passwords for services that do not offer passkey functionality yet.
For the short term, passwords are here to stay.
This is a contribution from Fox-IT. Through this link you can learn more about the company’s services.

