A recent EvilProxy phishing campaign attacked thousands of Microsoft 365 accounts worldwide. C-level accounts in particular were targeted to penetrate deeper into organizational structures.
During the months of March through June this year, the EvilProxy phishing campaign attacked thousands of Microsoft 365 accounts. In total, this involved a deluge of as many as 120,000 phishing emails to more than 100 companies and organizations worldwide.
According to Proofpoint researchers, the goal of the large phishing campaign was to target primarily C-level accounts. With access to these accounts, hackers could more easily attack deeper corporate systems.
Combination of attack methods
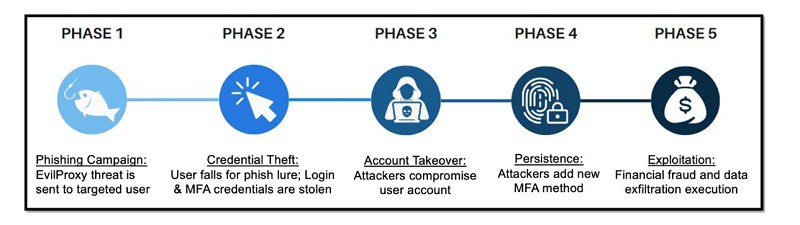
The phishing campaign used a combination of attack methods, including impersonating a fake brand, blocking malware scans and a multi-step infection chain. Its aim is mainly to take over the cloud accounts of C-level individuals. 39 percent of the cases involved CFOs and CEOs.
The use of EvilProxy, a phishing-as-a-service service, shows that the hackers mainly use reverse proxy and cookie injection methods. This enables them to evade MFA.
Attack process
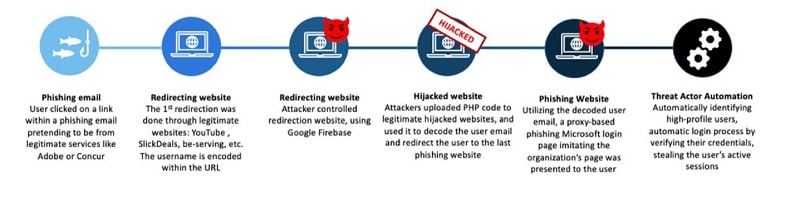
An attack begins by sending an e-mail as if it were coming from a well-known company, such as SAP Concur, DocuSign and Adobe. By clicking on links in these emails, a multi-step infection chain begins where user traffic is first sent to an open legitimate redirector, such as youTube. The traffic is then further redirected several times including malicious cookies and 404 redirects.
The traffic takes an unpredictable path, giving less chance of discovery that it is ultimately malicious traffic. Eventually, the traffic arrives at an EvilProxy phishing framework or landing page. This functions as a reverse proxy, pretends to be the receiving brand, and tries to impersonate a third-party identity provider, Proofpoint indicates.
Ultimately, this is how the hackers try to persistently insert themselves into the attacked systems and extort affected companies financially.
Robust security posture
Companies can guard against these types of very nasty attacks by actively monitoring for unusual traffic activity, emerging threats and potential vulnerabilities. In addition, companies should adopt a more robust cybersecurity posture.
Also read: Hackers succeed more to stay undetected in a corporate network