Palo Alto Networks’ Unit 42 published a new report outlining how the software supply chain has come to be seen as a threat to cloud security. The research unit conducted a red team exercise, with a large SaaS provider signed up with Palo Alto Networks.
Within three days, the team found critical software development flaws that could have exposed the organization tested to an attack, like the one suffered by Kaseya and SolarWinds.
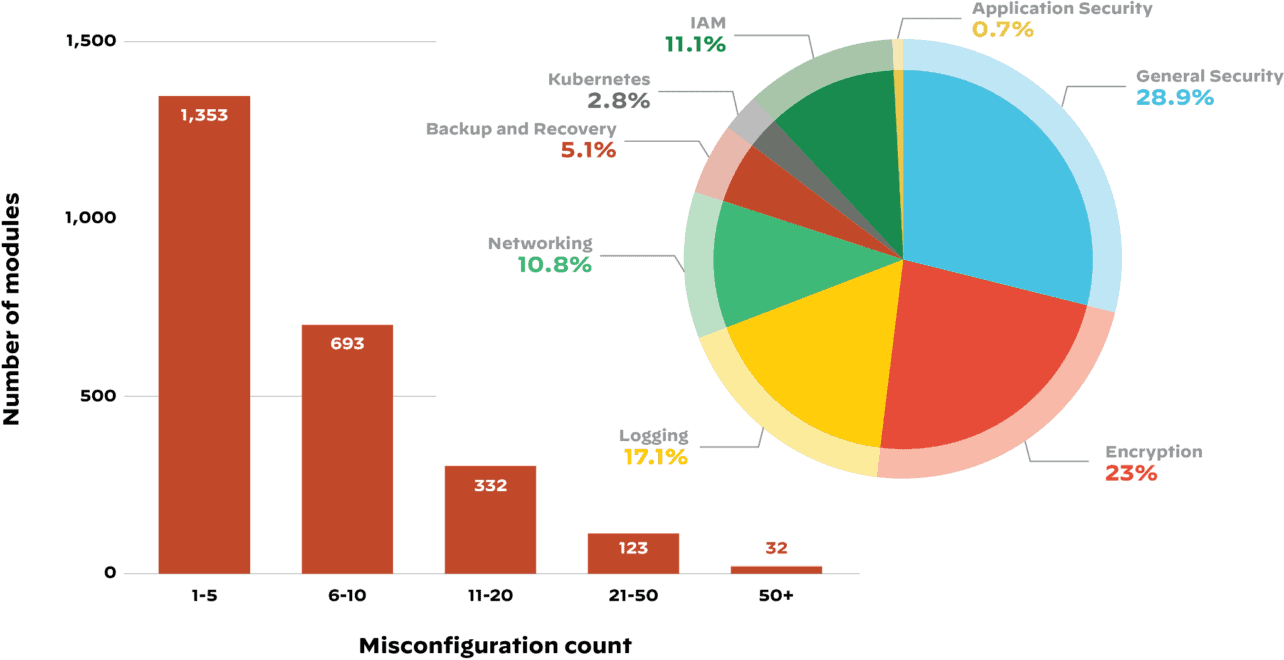
Unit 42 also found that 63% of third-party code used in building cloud infrastructure contained improper configuration.
Cloud infrastructure is not safe
If an attacker compromises third-party developers, it could be easy to breach thousands of organizations’ cloud infrastructure.
Palo Alto Networks analyzed data from various public data sources across the globe to come up with these conclusions about the threats organizations face from their software supply chains today. The findings say that 96% of third-party container applications deployed in cloud infrastructure have known vulnerabilities.
The report saw the Unit 42 researchers find that even for a customer with a mature security posture, there are still critical misconfigurations and flaws that allowed Unit 42 to take over the infrastructure within days.
The looming threat
In many supply chains attacks, an attacker compromises the vendor to insert malicious code in software customers use. Cloud infrastructure could fall to similar tactics especially if there is unvetted third-party code that could introduce flaws and allow breaches.
Unless the organizations can vet the code, it could come from anywhere, including an Advanced Persistent Threat.
The Unit draws attention to the problems in the security community, where DevOps has dropped the ball and the fact that it is easier to secure the entire cloud infrastructure than spend time chasing app-level bugs in millions of lines of code. It remains to be seen if the cloud is secure enough or if it will fall victim to crippling attacks.
