Google is increasingly cracking down on rogue apps posing as legitimate apps in its Play store. Recently, at the behest of ESET, a number of apps posing as legitimate Signal and Telegram apps were removed.
Google recently quietly removed a number of malicious apps from its Play store, following advice from ESET researchers. The malicious apps, when users performed certain actions, could intercept messages to and from both messaging platforms and other sensitive information.
Signal Plus Messenger and FlyGram
More specifically, this involved the Signal Plus Messenger app, which had been available for nine months and had been downloaded 100 times, and the FlyGram app for Telegram.
In addition to being in the tech app store, the first rogue app for Signal was/is also available in the Samsung app store and through the website signalplus. The app for Telegram was/is also available in all three channels.
BadBazaar Trojan
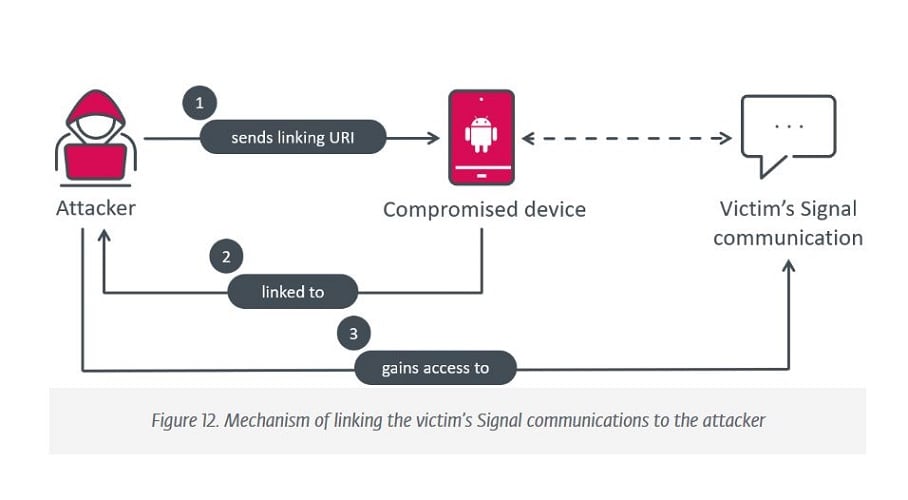
Under the hood, both rogue apps are built based on the open-source code of both messaging platforms. Embedded in this code is a spying Trojan BadBazaar attributed to the Chinese hacker group GREF. The spying tool specifically targets Uighurs, allegedly.
Through the trojan, the Signal Plus app was able to send messages and monitor contacts. This was based on users’ legitimate Signal number.
As a result, other sensitive information such as IMEI number, phone number, MAC address, telecom operator details, location data, Wi-Fi information, email for Google accounts, contact lists and PINs for text transfer were also forwarded.
Tip: Big Tech gets new rules from EU, what will you notice as a user?