Researchers at Intezer and BlackBerry discovered a new malware variant for Linux-based operating systems. Symbiote behaves like a parasite to evade detection.
The Linux malware latches onto operating systems’ processes. Ultimately, Symbiote allows hackers to intercept login data and set up backdoor access to (virtual) machines.
Infection
Symbiote’s infection process makes the malware unique. Typically, a standalone executable file is used to cause damage. In this case, the malware is loaded into all running processes as a shared object (SO). Once installed, Symbiote is able to hide and escape detection with various capabilities, including rootkit functionality.
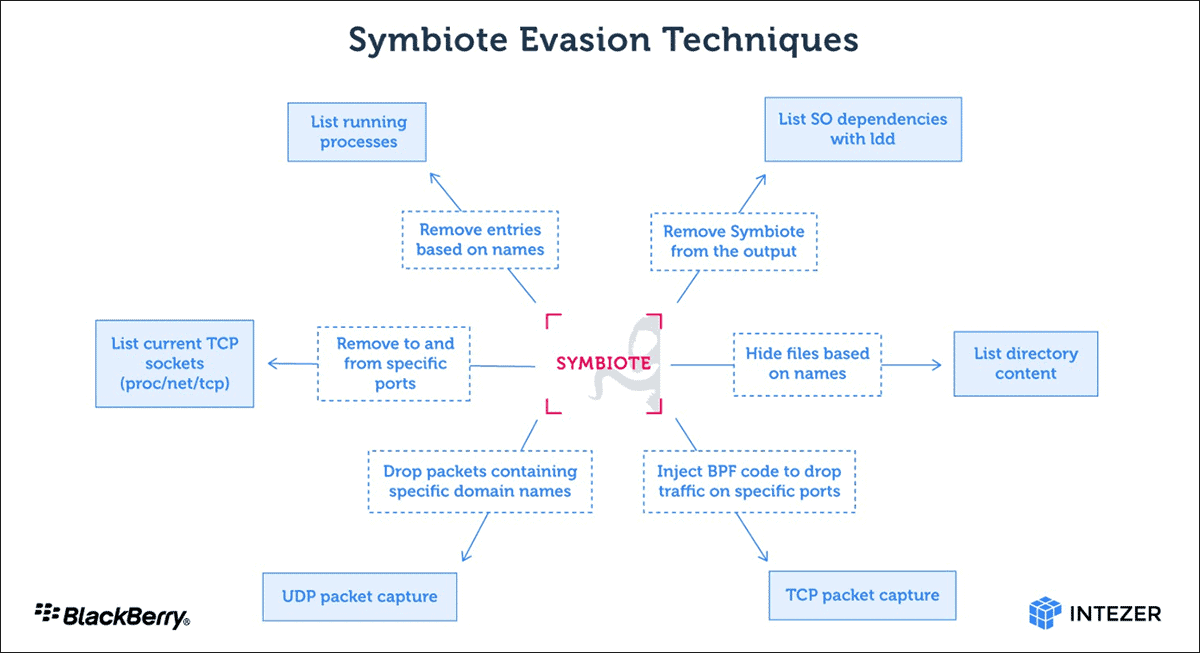
BFP functionality hides network traffic
Researchers from Intezer and BlackBerry discovered that the Symbiote malware hides not only in the file system, but the entire network. To do so, the malware uses Berkely Packet Filter (BPF) hooking. The functionality is activated when administrators boot any packet capture tool on an infected machine. In doing so, BPF bytecode is injected into the kernel to determine which packets should be ‘caught’. During the process, Symbiote adds its bytecode to filter out network traffic and remain invisible to the packet capture tool.
Targets
Researchers first caught glimpses of Symbiote at the beginning of this year. South-American banks were targeted in particular. Hackers are currently using stolen login data to impersonate Brazilian banks. Their customers are a likely target.
The researchers stated that Symbiote is one of the most advanced hacking methods they have found to date. Unfortunately, they expect this type of highly technical attack to increase significantly in the coming period.
Tip: BlackBerry releases Guard 2.0, focuses on XDR functionality



















