A fake Google Search result for the Cisco WebEx software causes victims to download the BatLoader malware. This malware, in turn, installs the DanaBot trojan.
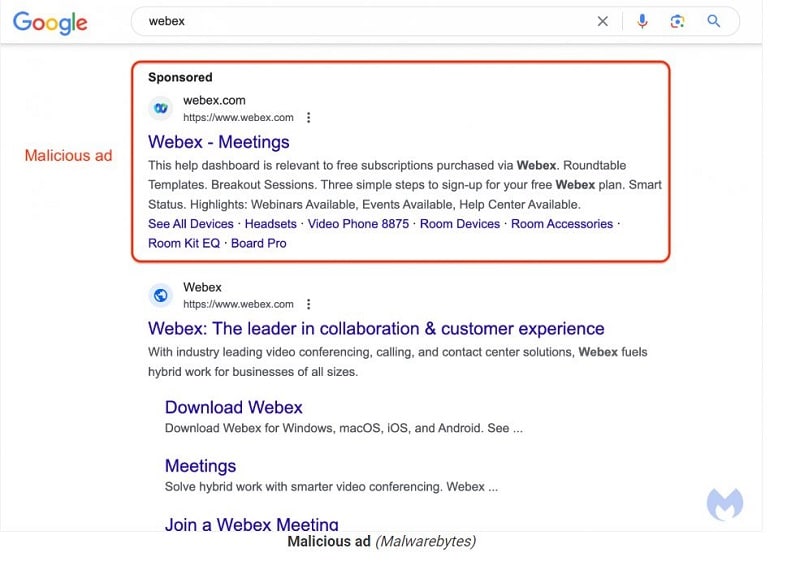
According to Malwarebytes’ security experts, a fake Google Ads campaign has been active for a week, providing a fake search result for the Cisco WebEx conferencing software in Google’s search engine. The spoofing of the WebEx search result is so professional that it can hardly be distinguished from the real site. Among other things, it uses the real WebEx logo and the legitimate URL “webex.com.
Security experts say the hackers are exploiting a loophole in Google Ads’ tracking template. The loophole allows them to provide other redirects while simply adhering to Google’s terms of use.
Redirects are source of malware
The Google Ads platform uses tracking templates with URL parameters that define a “final URL” based on information about the device used, location and other metrics for interaction opportunities. In this process, the URL displayed in an ad and the final URL destination must be linked to the same domain.
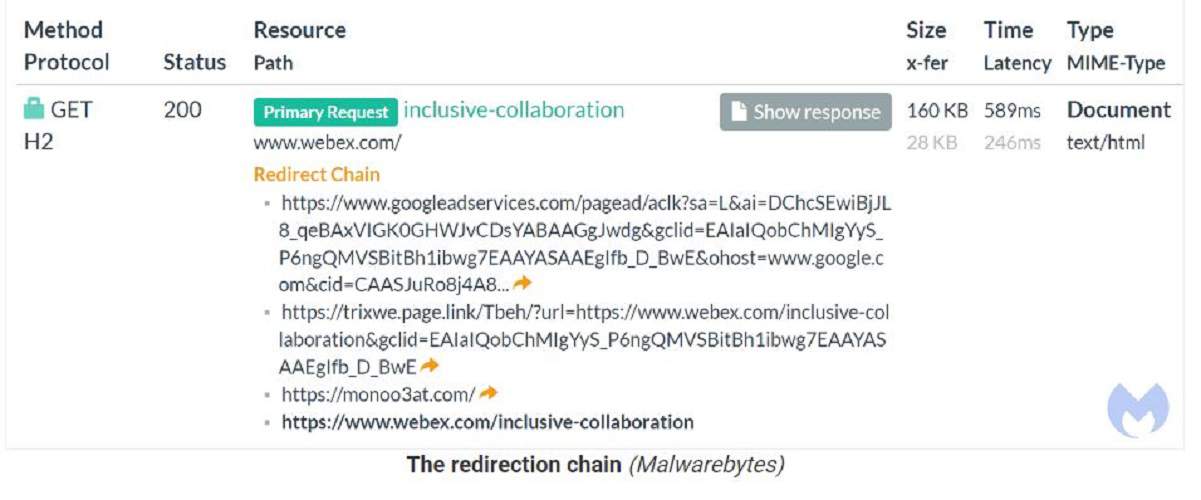
However, it is possible to redirect users to a website outside the set domain without restrictions. In this case, users are redirected to a website controlled by the hackers, which installs malware instead of the Cisco WebEx conferencing software. They used a Firebase URL (“trixwe.page.link”) as a tracking template with the final URL ‘www.webex.com’. By redirecting, the original URL ended up at the malware site ‘webexadvertisingoffer[.]com’.
Interestingly, some users who clicked on the site were filtered out. The hackers did not wish to serve users by protecting themselves with a sandbox. All these non-interesting clickers were simply redirected to the original WebEx site.
Installation BatLoader malware
When victims unexpectedly land on the malware site, the BatLoader malware is installed. This malware, in turn, installs the DanaBot trojan.
With this banking trojan, the hackers primarily steal passwords and can take screenshots, download ransomware modules, mask malicious C2 traffic and provide direct access to compromised hosts via HVNC.
In a response, Google says it always puts the security of its search results first. Meanwhile, action was reportedly taken against the malicious result. Cisco did not comment.
Also read: Google Chrome offers real-time phishing protection